At 8:47 AM on a Tuesday morning, Sarah Martinez, owner of a Hartford accounting firm, clicked what looked like an invoice from a trusted client. Within 23 seconds, her entire business network was locked down. Every file encrypted. Every backup compromised. The ransomware demand? $50,000 in Bitcoin, or lose seven years of client data forever.
Sarah's story isn't unique. It's happening to Connecticut small businesses every single day, and it's getting worse. AI-powered ransomware now launches 4,000 attacks per day across the United States, with small businesses bearing 43% of the burden. The attackers aren't just smarter: they're automated, relentless, and specifically targeting businesses that rely on basic antivirus as their only line of defense.
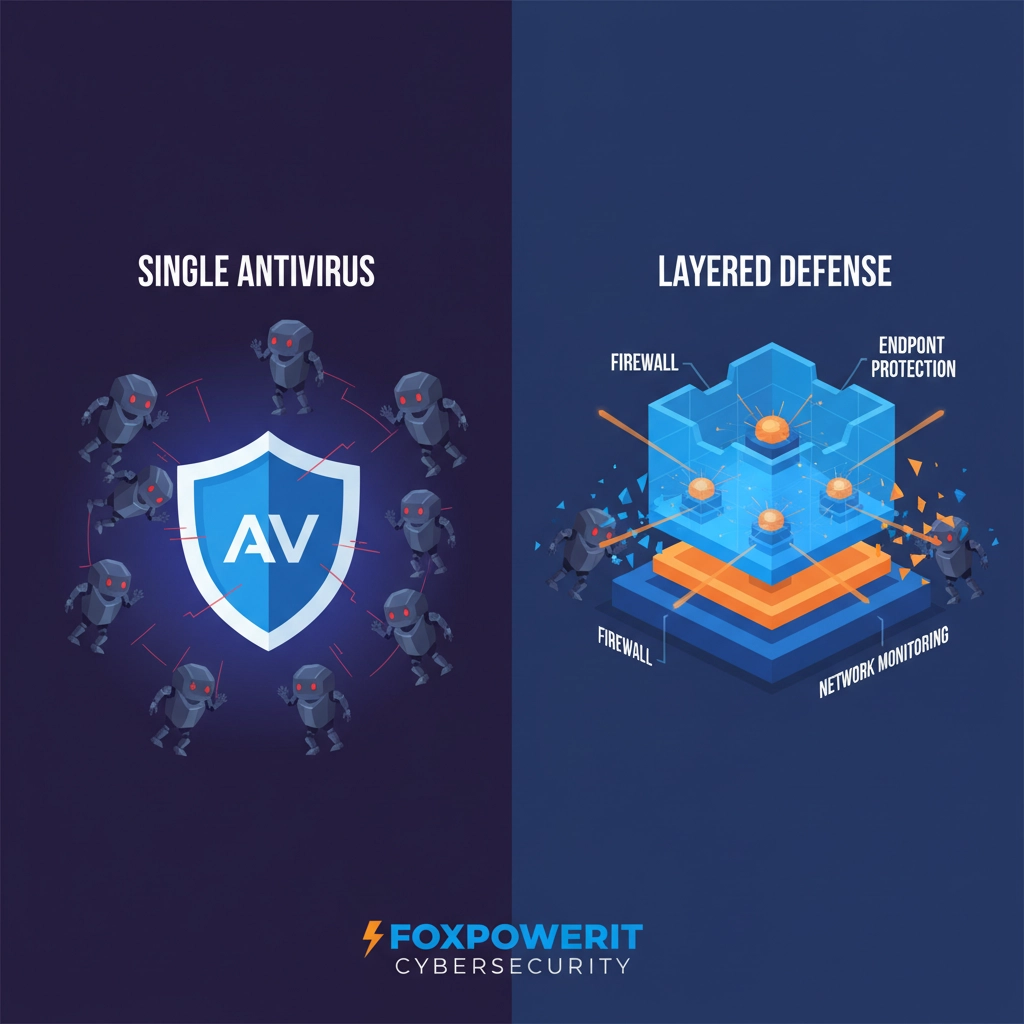
Here's the hard truth: if your Connecticut small business is still depending on basic antivirus software alone, you're not just vulnerable: you're a prime target. AI-driven ransomware treats single-layer security like a screen door in a hurricane. But there's a better way to protect your business, your clients, and your livelihood.
The solution isn't more antivirus software. It's defense in depth cybersecurity: a comprehensive approach that transforms your business from an easy target into a fortress that AI attackers will bypass for softer prey.
The Fatal Flaw in Basic Antivirus Protection
Most Connecticut small business owners understand they need antivirus software. What they don't realize is that modern cybercriminals: especially AI-powered ones: view traditional antivirus as a minor inconvenience, not a meaningful obstacle.
Basic antivirus operates on a simple premise: it maintains a database of known malware signatures and blocks files that match those patterns. Think of it like a security guard at your front door who only recognizes criminals from old wanted posters. If someone shows up wearing a disguise or commits a crime that's never been seen before, they walk right in.

This signature-based approach worked reasonably well in the 1990s and early 2000s, when malware was relatively static and cybercriminals were mostly individual hackers creating viruses for notoriety. But today's threat landscape is fundamentally different. AI-driven ransomware can:
- Generate thousands of unique variants in minutes, making signature detection useless
- Learn from failed attacks in real-time, adapting its approach to bypass defenses
- Operate completely in memory, leaving no files for antivirus to scan
- Disguise itself as legitimate business software, fooling even updated signature databases
- Coordinate multi-vector attacks that hit your network from several directions simultaneously
Consider what happened to a Stamford-based construction company in March 2024. Their antivirus software was fully updated and running active scans. The AI ransomware still succeeded by using three tactics simultaneously: a phishing email that looked like a legitimate Microsoft update, a USB device infected with malware that activated when plugged in, and a vulnerability in their router firmware that allowed remote access. The antivirus only detected the third attack vector: after the damage was done.
The fundamental problem is that basic antivirus is reactive, not proactive. It can only protect against threats it already knows about, while AI-powered attackers are specifically designed to be unpredictable and adaptive. This mismatch isn't just a technical limitation: it's a business catastrophe waiting to happen.
The Connecticut Small Business Vulnerability Gap
Connecticut small businesses face unique cybersecurity challenges that make relying on basic antivirus even more dangerous:
Geographic Targeting: Connecticut's proximity to major metropolitan areas like New York and Boston makes it an attractive target for cybercriminals. The state's high concentration of financial services, healthcare, and professional service businesses means attackers know there's valuable data to steal and businesses with the means to pay ransoms.
Regulatory Pressure: Connecticut businesses often handle sensitive data subject to state and federal privacy regulations. A successful ransomware attack doesn't just cost money: it can trigger regulatory penalties, lawsuits, and mandatory breach notifications that destroy business reputations.
Limited IT Resources: Most Connecticut small businesses don't have dedicated IT staff, making them dependent on whatever security software came pre-installed on their computers or whatever their nephew "who's good with computers" recommended. This ad-hoc approach creates security gaps that AI attackers actively scan for and exploit.
Interconnected Supply Chains: Connecticut's business ecosystem is highly interconnected. When one company gets compromised, the attack often spreads to customers, vendors, and business partners. Basic antivirus provides no protection against these lateral movements through business networks.
Understanding Defense in Depth Cybersecurity
Defense in depth cybersecurity operates on a completely different philosophy: instead of relying on a single security tool to stop all threats, it creates multiple independent layers of protection that work together to detect, prevent, and respond to attacks.
Think of it like securing a medieval castle. You wouldn't just put a lock on the front gate and call it protected. Instead, you'd build:
- A moat around the perimeter (network firewall)
- High walls with watchtowers (intrusion detection systems)
- Guards at multiple checkpoints (endpoint protection)
- Secure storage for valuables (data encryption)
- Communication systems for coordinating defense (security monitoring)
- Protocols for responding to attacks (incident response planning)
If attackers breach one layer, they immediately encounter the next. More importantly, each layer provides intelligence about the attack that helps strengthen the overall defense.

The Three Pillars of Defense in Depth
Administrative Controls: These are the policies, procedures, and training that govern how your organization handles cybersecurity. Examples include:
- Employee cybersecurity training programs
- Password management policies
- Incident response procedures
- Regular security assessments
- Data backup and recovery plans
- Access control policies that limit who can access sensitive information
Physical Controls: These protect the physical infrastructure that houses your digital assets:
- Secured server rooms with restricted access
- Surveillance systems monitoring critical infrastructure
- Environmental controls preventing hardware damage
- Secure disposal of old equipment containing sensitive data
- Visitor access controls and monitoring
Technical Controls: These are the technology solutions that actively monitor, prevent, and respond to cyber threats:
- Next-generation firewalls that inspect all network traffic
- Endpoint detection and response (EDR) tools that monitor individual devices
- Network segmentation that isolates critical systems
- Multi-factor authentication requiring multiple verification methods
- Behavioral analytics that detect unusual user activity
- Automated threat response systems that can isolate compromised devices
How Defense in Depth Defeats AI-Driven Ransomware
AI-powered ransomware succeeds by finding and exploiting the weakest link in your security chain. Defense in depth eliminates the concept of a "weakest link" by ensuring that no single failure can compromise your entire business.
Here's how it works in practice against a typical AI ransomware attack:
Phase 1 – Initial Access Attempt: The AI ransomware tries to enter your network through a phishing email. Your email security system (first layer) detects suspicious patterns and quarantines the message. Even if it gets through, employee training (administrative layer) means your team knows not to click suspicious links.
Phase 2 – Lateral Movement: If the ransomware somehow gains initial access, it tries to spread through your network. Network segmentation (technical layer) prevents it from accessing critical systems, while behavioral monitoring detects unusual network activity and alerts your IT team.
Phase 3 – Encryption Attempt: When the ransomware tries to encrypt your files, endpoint protection tools detect the malicious behavior and automatically isolate the affected device. Meanwhile, your backup systems (administrative layer) ensure that even if some data gets encrypted, you have clean copies stored securely offline.
Phase 4 – Communication: The ransomware tries to communicate with its command-and-control servers to receive instructions or transmit stolen data. Your firewall blocks these communications, while network monitoring logs the attempt for forensic analysis.
The key insight is that defense in depth doesn't just stop attacks: it makes them visible, containable, and recoverable. Even if the AI ransomware succeeds in compromising one system, the layered approach prevents it from achieving its ultimate goal of encrypting all your business data.
Real-World Ransomware Scenarios: Basic Antivirus vs. Defense in Depth
To understand the practical difference between these approaches, let's examine three real-world attack scenarios based on actual incidents affecting Connecticut businesses.
Scenario 1: The Trusted Vendor Attack
The Setup: A Bridgeport manufacturing company receives what appears to be an invoice from their longtime steel supplier. The email looks perfect: correct logo, sender address, and even references a recent order. The attached PDF contains an AI-generated ransomware payload that's never been seen before.
Basic Antivirus Response: The antivirus software scans the PDF attachment and finds no matching signatures in its database. Since this is a brand-new variant created by AI specifically for this attack, the file passes inspection. When the employee opens it, the ransomware activates immediately, encrypting the company's entire shared drive within 15 minutes. The antivirus never detects the threat because it's designed to be invisible to signature-based detection.
Defense in Depth Response: Multiple layers activate simultaneously:
- Email security analyzes the sender's behavior patterns and notices subtle inconsistencies in writing style compared to previous communications from the vendor
- The PDF attachment is automatically opened in a sandboxed environment, where its malicious behavior is detected before reaching the user's device
- Even if the file reached the endpoint, behavioral monitoring would detect the unusual file encryption activity and automatically quarantine the affected device
- Network segmentation ensures that even a compromised device cannot access critical manufacturing systems or financial data
- Offline backups remain untouched and available for immediate recovery
Outcome: Basic antivirus results in complete business shutdown for 2-3 weeks and $75,000 in recovery costs. Defense in depth contains the threat within minutes with minimal business impact.
Scenario 2: The Supply Chain Compromise
The Setup: A New Haven legal firm's managed service provider gets compromised by AI ransomware. The attackers use legitimate administrative credentials to access the law firm's network, appearing as authorized IT maintenance.
Basic Antivirus Response: Since the attackers are using legitimate credentials and tools, there's no malicious software for antivirus to detect. The ransomware spreads through the network for days, exfiltrating sensitive client data and mapping critical systems before finally activating the encryption routine. The antivirus remains silent because everything appears to be legitimate IT activity.
Defense in Depth Response: Administrative and technical controls catch the attack early:
- Privileged access monitoring notices that the MSP credentials are being used outside normal business hours and for unusual activities
- Behavioral analytics detect that the "IT administrator" is accessing files and systems they've never touched before
- Data loss prevention systems notice large amounts of sensitive data being transmitted to external locations
- Network segmentation prevents the attackers from accessing the most critical client files, even with administrative privileges
- Incident response procedures immediately revoke the compromised credentials and isolate affected systems
Outcome: Basic antivirus results in a massive data breach affecting hundreds of clients, regulatory penalties, and potential law firm closure. Defense in depth detects and stops the attack before significant data exposure occurs.
Scenario 3: The Zero-Day Exploit
The Setup: A Waterbury healthcare clinic gets targeted by AI ransomware that exploits a previously unknown vulnerability in their patient management software. The attack is completely silent and leaves no traces that signature-based detection could identify.
Basic Antivirus Response: The zero-day exploit is, by definition, unknown to antivirus databases. The attack proceeds undetected, encrypting patient records and demanding payment within 48 hours to avoid HIPAA violations and regulatory penalties. The practice faces potential closure if they cannot restore patient data quickly.
Defense in Depth Response: Multiple detection methods identify the threat:
- Application whitelisting prevents unauthorized software from running on critical healthcare systems
- Behavioral monitoring detects unusual process activity associated with the patient management software
- Network micro-segmentation isolates the patient records system from other clinic operations
- Automated backup systems maintain multiple copies of patient data in offline storage
- Incident response procedures include immediate coordination with healthcare compliance experts
Outcome: Basic antivirus results in potential HIPAA violations, regulatory penalties, and loss of patient trust. Defense in depth maintains business continuity and regulatory compliance throughout the incident.
The Connecticut Advantage: Local Compliance and Regulations
Connecticut small businesses operate in a complex regulatory environment that makes comprehensive cybersecurity not just good business practice, but legal necessity. The state's data protection laws, combined with federal regulations affecting many Connecticut industries, create compliance requirements that basic antivirus simply cannot address.
Connecticut Personal Data Act Requirements
Connecticut's Personal Data Act, which took effect in 2023, requires businesses to implement "reasonable security measures" to protect personal data. The law specifically mentions that businesses must consider:
- The sensitivity of the data being processed
- The size and complexity of the business
- The cost of implementing security measures
- The current state of technology and security practices
Basic antivirus fails this test in multiple ways. Courts and regulators increasingly view signature-based antivirus as outdated technology that doesn't constitute "reasonable security measures" given the current threat landscape. Businesses that suffer data breaches while relying only on basic antivirus may face regulatory penalties for inadequate protection.
Defense in depth cybersecurity, by contrast, demonstrates clear compliance with Connecticut's requirements by implementing multiple technical, administrative, and physical controls appropriate for the business size and data sensitivity.
Industry-Specific Regulations
Many Connecticut small businesses operate in heavily regulated industries that require specific cybersecurity measures:
Healthcare (HIPAA): Connecticut has over 8,000 healthcare practices that must comply with HIPAA security requirements. The regulation specifically requires multiple types of controls including access controls, audit controls, integrity controls, person authentication, and transmission security. Basic antivirus addresses none of these requirements, while defense in depth provides comprehensive HIPAA compliance support. FoxPowerIT's compliance assistance services help healthcare practices implement HIPAA-compliant security frameworks.
Financial Services: Connecticut's significant financial sector must comply with regulations like SOX, PCI-DSS, and state banking requirements. These regulations mandate specific security controls that go far beyond basic malware protection. Defense in depth provides the comprehensive control framework these businesses need.
Legal Services: Connecticut law firms handle sensitive client information subject to attorney-client privilege and state bar ethical requirements. Data breaches can result in both regulatory penalties and malpractice liability. Defense in depth helps firms maintain the confidentiality protections their professional obligations require.
Municipal and State Contract Requirements
Many Connecticut small businesses work with state and local governments, which increasingly require contractors to meet specific cybersecurity standards. The Connecticut Office of the Chief Information Officer has published cybersecurity requirements for state contractors that include:
- Regular vulnerability assessments
- Incident response capabilities
- Employee security training
- Multi-factor authentication
- Network segmentation
- Continuous monitoring
Basic antivirus meets none of these requirements. Businesses relying on signature-based protection may find themselves unable to bid on government contracts or maintain existing agreements.
Implementation Guide: Building Defense in Depth for Your Connecticut Small Business
Implementing defense in depth might seem overwhelming, but it doesn't have to be an all-or-nothing proposition. Connecticut small businesses can build comprehensive protection gradually, starting with the highest-impact, most cost-effective measures and adding layers over time.
Phase 1: Foundation (Months 1-2)
Administrative Controls – Start Here
- Implement mandatory password manager for all employees (cost: $3-5 per employee per month)
- Establish monthly cybersecurity training program (cost: $10-20 per employee per month)
- Create incident response plan specific to your business operations
- Establish daily backup procedures with offline storage components
- Document all systems and create network inventory
Physical Controls
- Secure server room or equipment area with locks and access logging
- Install security cameras monitoring critical infrastructure
- Implement clean desk policies for sensitive information
- Secure disposal procedures for old equipment and documents
Basic Technical Controls
- Deploy next-generation firewall to replace consumer-grade router (cost: $1,500-3,000)
- Implement multi-factor authentication for all business systems (cost: $1-3 per user per month)
- Enable endpoint logging and monitoring (cost: $5-10 per device per month)
Expected Investment: $5,000-8,000 initial setup, $200-500 monthly per 10-person business
Phase 2: Detection and Response (Months 3-4)
Enhanced Monitoring
- Deploy security information and event management (SIEM) system for centralized logging
- Implement behavioral analytics to detect unusual user activity
- Set up automated alerting for suspicious network activity
- Establish 24/7 security monitoring through managed security services
Network Segmentation
- Separate guest networks from business operations
- Isolate critical systems like financial software and customer databases
- Implement virtual LANs (VLANs) to control traffic flow
- Deploy network access control to manage device connections
Endpoint Protection Upgrade
- Replace basic antivirus with endpoint detection and response (EDR) solutions
- Implement application whitelisting for critical systems
- Deploy behavioral monitoring on all business devices
- Set up automated quarantine procedures for suspected compromises
FoxPowerIT's network monitoring and VLAN configuration services can help Connecticut businesses implement these technical controls efficiently.
Expected Investment: $3,000-5,000 additional setup, $300-700 additional monthly
Phase 3: Advanced Protection (Months 5-6)
Threat Intelligence Integration
- Subscribe to threat intelligence feeds relevant to your industry
- Implement automated threat hunting capabilities
- Deploy advanced malware analysis tools
- Set up threat correlation across multiple data sources
Data Protection Enhancement
- Implement data encryption for sensitive information at rest and in transit
- Deploy data loss prevention (DLP) systems to monitor information flows
- Set up privileged access management for administrative accounts
- Create air-gapped backup systems for critical data
Business Continuity Integration
- Develop comprehensive disaster recovery procedures
- Test backup and recovery systems monthly
- Create alternate work procedures for cyberattack scenarios
- Establish communication protocols for security incidents
Expected Investment: $2,000-4,000 additional setup, $200-400 additional monthly
Total Investment Analysis
For a typical 10-person Connecticut small business, comprehensive defense in depth implementation costs approximately:
- Initial Setup: $10,000-17,000 over six months
- Ongoing Monthly: $700-1,600 per month
- Annual Total: $18,400-36,200 per year
While this may seem significant, consider the alternative costs:
- Average ransomware recovery: $50,000-150,000 per incident
- Business downtime: $8,000-25,000 per day for small businesses
- Regulatory penalties: $10,000-100,000+ depending on violation
- Customer loss: 60% of small businesses close within 6 months after major cyberattack
Defense in depth pays for itself by preventing just one successful attack.
Choosing the Right Partner: Managed IT Services vs. DIY Implementation
Most Connecticut small businesses lack the internal expertise to implement and maintain defense in depth cybersecurity effectively. This reality creates two viable paths: build internal capabilities or partner with a managed IT services provider.
The DIY Challenge
Implementing defense in depth internally requires significant ongoing investment:
- Personnel: Hiring qualified cybersecurity staff costs $75,000-120,000 annually in Connecticut
- Training: Keeping staff current with evolving threats requires 40-60 hours per year of specialized training
- Tools: Enterprise security tools often require expensive per-seat licensing and dedicated hardware
- Time: Proper security monitoring requires 24/7 attention that small businesses rarely can provide
Most importantly, cybersecurity is not a "set it and forget it" solution. Threats evolve daily, new vulnerabilities emerge constantly, and security tools require continuous tuning and updating. Few small businesses have the resources to maintain this level of ongoing vigilance.
The Managed Services Advantage
Partnering with a Connecticut-based managed IT services provider like FoxPowerIT offers several advantages:
Cost Efficiency: Sharing cybersecurity expertise across multiple clients reduces per-business costs compared to hiring internal staff. A comprehensive managed security program typically costs 50-70% less than building equivalent internal capabilities.
Specialized Expertise: Managed services providers maintain teams of specialists who focus exclusively on cybersecurity, staying current with the latest threats and defensive technologies.
24/7 Monitoring: Professional security operations centers provide round-the-clock monitoring and response capabilities that internal teams rarely can match.
Compliance Support: Experienced MSPs understand Connecticut's regulatory environment and can help ensure your defense in depth implementation meets all applicable requirements.
Scalability: As your business grows, managed services can scale your security program without requiring major internal investments or hiring.
FoxPowerIT's managed IT services provide Connecticut small businesses with enterprise-level defense in depth protection without the complexity and cost of building internal security teams.
Hybrid Approaches
Some larger small businesses choose a hybrid model, maintaining internal IT staff for day-to-day operations while partnering with managed security providers for specialized cybersecurity functions. This approach can work well for businesses with 25+ employees that already have IT infrastructure in place.
Beyond Protection: The Business Benefits of Defense in Depth
While preventing ransomware attacks is the primary goal, defense in depth cybersecurity provides additional business benefits that basic antivirus cannot match.
Competitive Advantage Through Trust
Connecticut businesses that can demonstrate comprehensive cybersecurity measures gain competitive advantages:
- Customer Confidence: Clients increasingly ask about cybersecurity measures before sharing sensitive data
- Partner Requirements: Many larger companies now require their vendors to meet specific cybersecurity standards
- Insurance Savings: Comprehensive cybersecurity can reduce cyber liability insurance premiums by 20-40%
- Contract Opportunities: Government and enterprise contracts often require specific security certifications
Operational Efficiency Improvements
Defense in depth implementations often improve overall business operations:
- Network Performance: Modern security tools provide network optimization alongside protection
- System Reliability: Proactive monitoring identifies and resolves issues before they impact productivity
- Remote Work Support: Comprehensive security enables safe remote and hybrid work arrangements
- Process Documentation: Security implementations require documenting systems and procedures, improving overall business organization
Future-Proofing Your Business
As cyber threats continue evolving, businesses with defense in depth are better positioned to adapt:
- Scalable Security: Layered approaches can accommodate business growth without complete overhauls
- Technology Integration: Modern security platforms integrate with business applications to enhance rather than hinder operations
- Regulatory Compliance: Comprehensive security frameworks adapt more easily to changing regulatory requirements
- Investment Protection: Quality security implementations provide value for years, while basic antivirus becomes obsolete quickly
Taking Action: Your Next Steps
The choice between basic antivirus and defense in depth cybersecurity isn't really a choice at all: it's a necessity for Connecticut small businesses that want to survive and thrive in today's threat environment.
AI-driven ransomware attacks will only become more sophisticated, more targeted, and more damaging. Businesses that continue relying on single-layer protection are gambling with their survival. Those that implement comprehensive defense in depth are building resilience that protects their operations, their customers, and their futures.
Immediate Action Plan
This Week:
- Audit your current security measures to identify gaps
- Research managed IT services providers in Connecticut
- Calculate the true cost of a successful ransomware attack on your business
- Begin employee security awareness training immediately
This Month:
- Implement password managers and multi-factor authentication
- Establish daily backup procedures with offline components
- Schedule a comprehensive cybersecurity assessment
- Create an incident response plan for your business
Next Quarter:
- Partner with a qualified managed services provider for defense in depth implementation
- Begin network segmentation and monitoring deployment
- Upgrade from basic antivirus to comprehensive endpoint protection
- Test your backup and recovery procedures
Connecticut small businesses can no longer afford to treat cybersecurity as an IT problem: it's a business survival issue. Defense in depth isn't just better protection than basic antivirus; it's the difference between remaining in business after an attack and closing your doors forever.
The AI-powered attackers are already targeting your industry, your geographic area, and businesses exactly like yours. The question isn't whether you'll face a sophisticated cyberattack: it's whether you'll be prepared when it comes.
Don't wait for the attack to happen. Contact FoxPowerIT today to learn how defense in depth cybersecurity can transform your Connecticut small business from an easy target into a protected, resilient operation that attackers will pass by for softer prey. Your business, your employees, and your customers deserve nothing less than comprehensive protection in today's dangerous digital landscape.

