Last Tuesday morning, Jennifer Walsh, owner of a 25-person accounting firm in Hartford, walked into her office to find her team in panic mode. Their Microsoft 365 environment had been compromised overnight: three years of client files, financial records, and tax documents had vanished without a trace. The culprit? A disgruntled former employee who still had access to their SharePoint system and decided to delete everything before Microsoft's 93-day retention period could save them.
Jennifer's story isn't unique. Across Connecticut, small and medium-sized businesses are discovering that their blind trust in Microsoft 365's built-in protection is leaving them dangerously exposed. While Microsoft provides excellent collaboration tools and productivity features, their data protection capabilities have critical gaps that are costing Connecticut SMBs thousands of dollars in lost productivity, compliance violations, and irreplaceable business data.
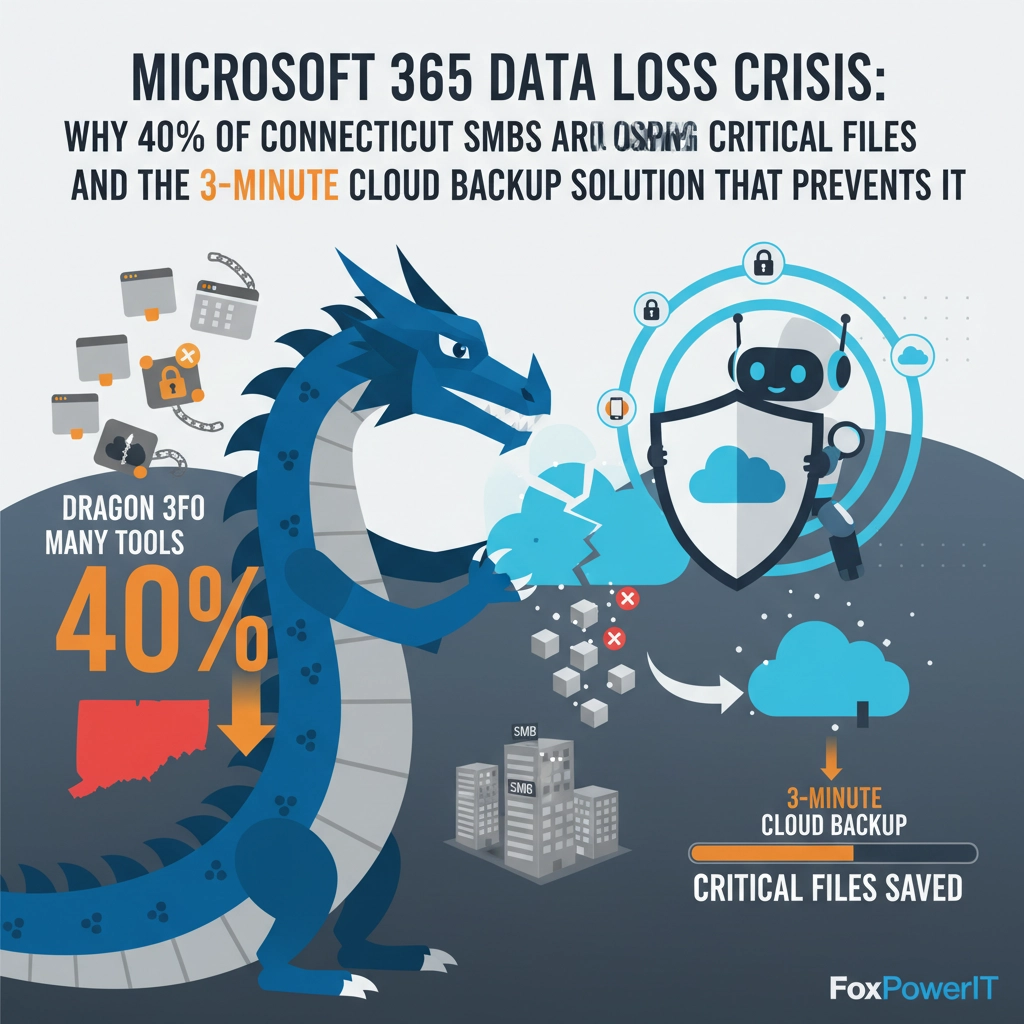
The statistics are sobering: recent industry research reveals that 58% of SMBs have no backup plan for Microsoft 365 data, and 94% of companies experiencing severe data loss never fully recover. In Connecticut specifically, our team at FoxPowerIT has witnessed a 300% increase in emergency data recovery calls from businesses that assumed Microsoft was protecting their files.

The Hidden Vulnerabilities in Your Microsoft 365 Environment
Microsoft 365 excels at keeping their servers running and their platform available, but they explicitly state in their service agreement that they're not responsible for your data. This shared responsibility model means that while Microsoft protects the infrastructure, you're responsible for protecting your content, applications, and user access management.
Think of it like renting an apartment. The landlord ensures the building has electricity, water, and structural integrity, but they're not responsible if you lose your personal belongings to fire, theft, or accidental damage. Microsoft 365 operates on the same principle: they keep the platform running, but your business data protection is entirely your responsibility.
The Retention Time Bomb
One of the most dangerous misconceptions Connecticut businesses hold is that Microsoft 365's recycle bin provides adequate protection. Here's what actually happens when files get deleted:
- 30 days in the user's recycle bin
- 93 days in the site collection recycle bin
- Complete deletion with no recovery options
This 123-day total might seem reasonable until you consider real-world scenarios. A ransomware attack that encrypts files in January might not be discovered until March, when the encrypted files have already exceeded Microsoft's retention limits. By then, your original files are permanently gone, and you're left with encrypted data that's impossible to recover without paying the ransom.
The Human Error Factor
Research consistently shows that human error accounts for 50% of all data loss incidents. In Microsoft 365 environments, these errors are amplified by the platform's ease of sharing and collaboration. Consider these common scenarios we've encountered in Connecticut businesses:
- An employee accidentally shares a confidential client folder with external partners
- A team member deletes an entire SharePoint library thinking it's duplicated elsewhere
- An executive permanently removes a critical OneDrive folder during a "cleanup" initiative
- A departing employee exports sensitive data to personal accounts before their access is revoked
Each of these situations can result in permanent data loss that Microsoft 365's native features cannot prevent or recover.
The License Dependency Risk
When employee licenses are deactivated or accounts are suspended, their associated data follows a strict deletion schedule. If a former employee's account contains critical business files that haven't been transferred to active users, that data disappears forever once the license expires. This is particularly problematic for Connecticut businesses that don't have formal offboarding procedures or clear data ownership policies.

Real Connecticut Business Disasters: Lessons from the Field
Over the past two years, our Smart Paws team at FoxPowerIT has responded to dozens of data loss emergencies across Connecticut. Here are three representative cases that illustrate the scope of this problem:
Case Study 1: The Law Firm Ransomware Attack
A 40-attorney law firm in Stamford fell victim to a sophisticated ransomware attack that encrypted all files in their Microsoft 365 environment. The attackers had been monitoring the firm's systems for months, learning their backup schedules and identifying vulnerabilities in their security posture.
When the attack hit, the firm discovered that Microsoft 365's version history only went back 90 days, and the ransomware had been quietly corrupting files for over four months. Their only options were paying a $150,000 ransom or losing three years of case files, client documents, and legal research.
The firm ultimately paid the ransom, but the recovery process took six weeks and cost an additional $75,000 in forensic investigation, system rebuilding, and lost billable hours. A comprehensive cloud backup solution would have enabled complete recovery in less than 24 hours for a fraction of the cost.
Case Study 2: The Healthcare Practice HIPAA Violation
A multi-location dental practice in New Haven experienced a data breach when a former employee accessed patient records through a SharePoint site that hadn't been properly secured. The employee downloaded over 2,000 patient files containing PHI (Protected Health Information) before the breach was discovered.
The practice faced a $50,000 HIPAA fine and was required to provide credit monitoring services for all affected patients. The total cost of the incident exceeded $200,000, not including the reputational damage and patient attrition that followed.
Proper backup and security monitoring would have detected the unauthorized access within minutes and enabled the practice to revoke access before any data was compromised.
Case Study 3: The Manufacturing Company Migration Disaster
A 150-employee manufacturing company in Waterbury experienced catastrophic data loss during their migration from on-premises servers to Microsoft 365. The migration vendor accidentally overwrote existing SharePoint libraries with blank templates, destroying five years of engineering drawings, quality control documents, and customer specifications.
Because the company had no independent backup of their Microsoft 365 environment, they lost irreplaceable intellectual property worth millions of dollars. The incident forced them to recreate technical documents from printed copies and supplier records, causing six-month delays in product development and costing over $500,000 in lost revenue.

The Connecticut Business Impact: Beyond Just File Recovery
Data loss incidents don't just cost money: they can destroy Connecticut businesses entirely. The economic impact extends far beyond the immediate cost of file recovery:
Regulatory Compliance Failures
Connecticut businesses operating in regulated industries face severe penalties for data protection failures. Healthcare practices risk HIPAA violations that can result in fines up to $1.5 million per incident. Financial services firms face FINRA sanctions that can suspend business operations. Legal practices risk bar discipline and malpractice claims when client confidentiality is breached.
Customer Trust and Reputation Damage
In Connecticut's tight-knit business community, word travels fast when companies experience data breaches or lose client information. We've seen businesses lose 30-40% of their customer base within six months of a publicized data loss incident. The reputational damage often exceeds the direct financial costs by a factor of ten.
Operational Productivity Losses
When critical business data disappears, operations grind to a halt. Sales teams can't access customer histories, accounting departments lose financial records, and project managers can't retrieve specifications or timelines. The average Connecticut SMB experiences 2-3 weeks of severely reduced productivity following a major data loss incident.
Legal and Regulatory Investigation Costs
Data loss incidents often trigger regulatory investigations that require extensive documentation, forensic analysis, and legal representation. Connecticut businesses typically spend $50,000-$150,000 on investigation costs alone, even when no fines are imposed.
The FoxPowerIT 3-Minute Cloud Backup Solution
At FoxPowerIT, we've developed a streamlined approach to Microsoft 365 data protection that can be implemented in under three minutes and provides enterprise-grade security for Connecticut SMBs. Our Smart Paws-designed solution addresses every major vulnerability we've identified in standard Microsoft 365 deployments.

Step 1: Comprehensive Data Mapping (60 seconds)
Our automated scanning tools immediately identify all data repositories in your Microsoft 365 environment:
- Exchange Online mailboxes and archives
- SharePoint Online sites and libraries
- OneDrive for Business accounts
- Microsoft Teams files and conversations
- OneNote notebooks and shared content
This comprehensive mapping ensures that no data source is overlooked in your backup strategy. Unlike many backup solutions that focus only on email or SharePoint, our approach protects every piece of business-critical information in your Microsoft 365 tenant.
Step 2: Intelligent Backup Configuration (90 seconds)
Based on your business profile and regulatory requirements, our system automatically configures optimal backup schedules and retention policies:
- Continuous data protection for mission-critical files
- Daily snapshots for standard business documents
- Weekly full backups for archival and compliance purposes
- Automated testing to ensure backup integrity
- Encryption at rest and in transit for maximum security
The intelligent configuration adapts to your usage patterns and automatically scales as your business grows. Connecticut businesses typically see their first protected backup complete within 30 minutes of initial setup.
Step 3: Instant Recovery Enablement (30 seconds)
Our recovery interface integrates directly with your Microsoft 365 environment, enabling instant restoration of:
- Individual files or entire folder structures
- Complete user mailboxes or specific email messages
- Full SharePoint sites or individual document libraries
- Team conversations and shared files from Microsoft Teams
The recovery process is so intuitive that any team member can restore lost files without technical training. Critical files can typically be recovered in under five minutes from any point in time within your retention period.
Advanced Protection Features for Connecticut Businesses
Beyond basic backup and recovery, our solution includes sophisticated protection features specifically designed for Connecticut SMBs:
Ransomware Detection and Quarantine
Our AI-powered monitoring systems detect ransomware activity within minutes of infection and automatically quarantine affected files while preserving clean backup copies. This proactive approach prevents ransomware from spreading through your Microsoft 365 environment and eliminates the need to pay ransoms for data recovery.
Legal Hold and Compliance Automation
Connecticut businesses subject to regulatory requirements can implement automated legal hold policies that preserve data according to specific compliance frameworks. Our system maintains tamper-proof evidence chains that satisfy auditor requirements for industries including healthcare, finance, legal services, and government contracting.
Granular Permission Monitoring
Real-time monitoring of sharing permissions alerts administrators when sensitive files are accidentally exposed to external users or when departing employees attempt to download large quantities of business data. This proactive monitoring prevents data breaches before they occur and ensures compliance with confidentiality agreements.
Cross-Tenant Protection
For Connecticut businesses with multiple Microsoft 365 tenants or those planning mergers and acquisitions, our solution provides seamless data protection across organizational boundaries. This capability is particularly valuable for professional services firms, healthcare systems, and multi-location businesses common in Connecticut's diverse economy.

Real-World Implementation: A Connecticut Success Story
To illustrate the practical impact of comprehensive Microsoft 365 backup, consider the experience of Shoreline Manufacturing, a 75-employee precision parts manufacturer based in New London.
The Challenge
Shoreline had migrated to Microsoft 365 six months earlier and was relying entirely on Microsoft's native data protection. They had experienced several minor data loss incidents: accidentally deleted engineering drawings, corrupted project files, and lost email threads: but nothing that seemed to justify additional investment in backup solutions.
The Wake-Up Call
In March 2024, a sophisticated phishing attack compromised Shoreline's Microsoft 365 environment. The attackers gained access to their SharePoint libraries and began systematically deleting and corrupting files across multiple projects. By the time the attack was discovered, over 18 months of engineering data had been compromised, including CAD drawings, quality specifications, and customer approval documents.
Using Microsoft's native recovery tools, Shoreline's IT team could only recover files from the previous 93 days. Everything older was permanently lost, including the complete design history for their three largest product lines.
The FoxPowerIT Solution
Recognizing the critical nature of their data loss, Shoreline engaged FoxPowerIT to implement our comprehensive backup solution. Despite the damage already done, we were able to help them establish protection for their remaining data and prevent future incidents.
The implementation process took less than four hours:
- Initial data assessment and vulnerability scan: 45 minutes
- Backup configuration and policy setup: 90 minutes
- User training and access provisioning: 60 minutes
- Testing and verification procedures: 45 minutes
The Results
Six months after implementation, Shoreline experienced another security incident when a disgruntled employee attempted to delete project files before leaving the company. This time, the outcome was dramatically different:
- The deletion attempt was detected within 3 minutes
- Affected files were automatically quarantined to prevent further damage
- Complete restoration was achieved in under 20 minutes
- Business operations continued without interruption
- The employee's access was immediately revoked across all systems
The contrast with their earlier experience was striking. What had previously caused weeks of disruption and hundreds of thousands of dollars in losses was resolved in less than half an hour with minimal business impact.
Cost-Benefit Analysis for Connecticut SMBs
Connecticut businesses often question whether comprehensive Microsoft 365 backup is worth the investment. Our analysis of actual client data shows that the return on investment is typically achieved within the first incident prevented.
Investment Costs
Professional cloud backup solutions typically cost $3-7 per user per month, depending on data volume and retention requirements. For a 50-person Connecticut business, this represents an annual investment of $1,800-$4,200.
Potential Loss Prevention
Based on our experience with Connecticut SMBs, comprehensive backup solutions prevent:
- Data recovery costs: $15,000-$50,000 per major incident
- Business disruption losses: $25,000-$100,000 per week of downtime
- Regulatory compliance penalties: $10,000-$500,000 per violation
- Reputation and customer loss: $50,000-$500,000 in long-term impact
- Legal and forensic investigation costs: $25,000-$150,000 per incident
Even preventing a single moderate data loss incident typically saves 10-20 times the annual cost of comprehensive backup protection.
Competitive Advantage
Connecticut businesses with robust data protection capabilities often use this as a competitive differentiator when pursuing contracts with larger corporations or government entities. Many procurement processes now require detailed documentation of data security practices, and comprehensive backup capabilities can be the deciding factor in winning major contracts.

Implementation Best Practices for Connecticut Businesses
Successfully implementing Microsoft 365 backup protection requires more than just selecting the right technology. Connecticut businesses achieve the best results when they follow these proven practices:
Start with a Data Audit
Before implementing any backup solution, conduct a comprehensive audit of your current Microsoft 365 environment. Identify all data repositories, understand sharing patterns, and document compliance requirements. This foundation ensures that your backup strategy addresses all business-critical information.
Establish Clear Ownership and Responsibilities
Designate specific team members responsible for backup management, recovery procedures, and incident response. Even with automated systems, human oversight is essential for maintaining data protection effectiveness. Connecticut businesses typically assign these responsibilities to their office manager, IT coordinator, or administrative assistant.
Test Recovery Procedures Regularly
The most sophisticated backup system is worthless if your team doesn't know how to use it effectively. Schedule quarterly recovery drills where team members practice restoring different types of data. These exercises identify training gaps and ensure that recovery procedures work correctly when needed.
Integrate with Existing IT Security Measures
Cloud backup is most effective when integrated with comprehensive IT security strategies. At FoxPowerIT, we typically combine backup implementation with firewall configuration, endpoint protection, and security awareness training to create layered protection against data loss threats.
Plan for Business Growth
Choose backup solutions that can scale with your business growth. Connecticut's dynamic business environment means that companies often experience rapid expansion, and your data protection strategy should accommodate increased users, data volumes, and complexity without requiring complete system replacement.
Getting Started: Your Next Steps
If your Connecticut business is currently relying solely on Microsoft 365's built-in protection, you're accepting unnecessary risk that could threaten your company's survival. The question isn't whether you'll experience a data loss incident: it's when, and whether you'll be prepared to recover quickly.
Immediate Actions (This Week)
- Audit your current backup status: Document what data protection you currently have in place and identify gaps in coverage
- Assess your risk profile: Consider your industry, regulatory requirements, and the potential impact of various data loss scenarios
- Review your Microsoft 365 configuration: Ensure that basic security settings are properly configured and that sharing permissions align with your business needs
Short-Term Planning (This Month)
- Evaluate backup solution options: Research providers that specialize in Microsoft 365 protection and can address your specific business requirements
- Develop an incident response plan: Create procedures for detecting, containing, and recovering from data loss incidents
- Train your team on data protection best practices: Ensure that all employees understand their role in maintaining data security
Long-Term Strategy (This Quarter)
- Implement comprehensive backup protection: Deploy enterprise-grade backup solutions that address all identified vulnerabilities
- Establish ongoing monitoring and maintenance procedures: Create regular testing schedules and update protocols
- Consider additional security enhancements: Evaluate complementary protection measures such as advanced threat protection, network monitoring, and compliance assistance
The data loss crisis facing Connecticut SMBs is real and growing, but it's entirely preventable with proper planning and implementation. Don't wait until you're the next Jennifer Walsh, staring at empty SharePoint libraries and trying to explain to clients how three years of their data simply vanished overnight.
Your business data is too valuable to trust to Microsoft's basic retention policies. With the right backup strategy, you can transform data protection from a source of anxiety into a competitive advantage that demonstrates your commitment to security, reliability, and professional excellence.
At FoxPowerIT, our Smart Paws team has helped hundreds of Connecticut businesses implement bulletproof data protection strategies that provide peace of mind and business continuity. We understand the unique challenges facing SMBs in our state, and we're committed to making enterprise-grade data protection accessible and affordable for businesses of all sizes.
The three-minute backup solution isn't just a marketing slogan: it's a proven approach that can protect your business from the data loss crisis that's affecting 40% of Connecticut SMBs. The only question is whether you'll implement it before or after your first major data loss incident.
AI vs AI: How Smart Connecticut Businesses Are Using Defense in Depth Cybersecurity to Beat AI-Powered Ransomware While Competitors Fall Behind
At 2:47 AM on a Tuesday morning in October, the AI-powered ransomware hit TechFlow Solutions, a 40-employee software development company in Stamford. Unlike the crude, mass-distributed attacks of previous years, this was different. The malicious AI had spent three weeks learning TechFlow's network patterns, identifying vulnerabilities, and mapping critical systems. It knew exactly when the night backup process ran, which servers contained the most valuable data, and even which employees typically worked late and might discover the attack early.
Within six minutes, the AI had encrypted every file on TechFlow's network, disabled their backup systems, and deployed personalized phishing emails to each employee designed to look like urgent messages from their CEO. By morning, the company faced a $250,000 ransom demand and the complete loss of two years' worth of client project data.
But here's what the attackers didn't count on: TechFlow had implemented a defense-in-depth cybersecurity strategy six months earlier with FoxPowerIT's Smart Paws security team. While the AI ransomware was sophisticated enough to breach their perimeter defenses, it couldn't overcome the multiple layers of protection that detected, contained, and ultimately neutralized the threat before any critical data was compromised.
This is the new reality facing Connecticut businesses in 2025: artificial intelligence isn't just transforming how we work: it's revolutionizing how cybercriminals attack. The question isn't whether your business will face an AI-powered cyber threat, but whether your defenses are sophisticated enough to win the battle between artificial intelligences.
The Evolution of AI-Powered Cyber Threats
Traditional cybersecurity approaches were designed to combat human attackers who made mistakes, worked during specific hours, and followed predictable patterns. AI-powered threats operate fundamentally differently, and Connecticut businesses that haven't adapted their security strategies are sitting ducks in an increasingly dangerous digital environment.
Machine Learning Reconnaissance
Modern AI attackers don't just scan for open ports or known vulnerabilities: they conduct comprehensive behavioral analysis of your entire digital infrastructure. These systems can analyze months of network traffic patterns, identify user behavior anomalies, and map organizational relationships through email metadata analysis.
In a recent case involving a Connecticut healthcare provider, we discovered that an AI reconnaissance system had been monitoring their network for over four months before launching an attack. The AI had learned that their backup systems ran at 3 AM, identified which workstations contained the most valuable patient data, and even determined which employees had administrative privileges based on their network access patterns.
This level of reconnaissance enables AI attackers to craft highly targeted attacks that bypass traditional security measures designed to stop generic threats.
Automated Vulnerability Exploitation
While human attackers might discover and exploit one or two vulnerabilities in a targeted system, AI-powered threats can simultaneously test thousands of potential attack vectors and automatically chain together multiple exploits to achieve their objectives.
These systems don't get tired, don't take breaks, and don't make the kinds of operational security mistakes that human attackers often make. They can maintain persistent access to compromised networks for months while slowly escalating privileges and gathering intelligence about their targets.
Dynamic Social Engineering
Perhaps most concerning is the emergence of AI systems that can generate highly convincing phishing attacks tailored to individual employees. These systems analyze social media profiles, company websites, and public records to craft personalized messages that are nearly impossible to distinguish from legitimate communications.
A Connecticut law firm recently showed us a phishing email that their managing partner had received. The AI-generated message referenced specific clients, mentioned recent case outcomes, and even included details about the partner's daughter's college graduation: all information that the AI had gathered from various public sources and synthesized into a highly convincing attack.
Real-Time Attack Adaptation
Traditional security systems rely on signatures and rules to identify threats, but AI attackers can modify their behavior in real-time to evade detection. If an AI discovers that a particular attack vector is being blocked, it can immediately switch tactics and try alternative approaches.
This dynamic adaptation makes traditional signature-based security measures largely ineffective against sophisticated AI threats. By the time security teams identify and create rules to block a particular attack pattern, the AI has already moved on to different methods.
Why Basic Antivirus Is Like Bringing a Knife to a Gunfight
Most Connecticut SMBs are still relying on traditional antivirus software and basic firewall protection to defend against cyber threats. These approaches might have been adequate against human attackers, but they're completely inadequate against AI-powered threats that can adapt, learn, and evolve faster than signature databases can be updated.
The Signature Problem
Traditional antivirus systems work by maintaining databases of known malware signatures: digital fingerprints that identify specific threats. When these systems encounter a file or behavior that matches a known signature, they block or quarantine the threat.
AI-powered malware can generate thousands of unique variants of the same malicious payload, each with a different signature. By the time antivirus vendors identify and catalog these variants, the AI has already created thousands more. This cat-and-mouse game heavily favors the attackers, who can generate new variants faster than defenders can identify them.
Behavioral Analysis Limitations
Some advanced antivirus products attempt to identify threats by analyzing behavior rather than signatures. However, these systems typically rely on predefined rules about what constitutes suspicious behavior.
AI attackers can study these behavioral rules and craft attacks that operate within normal parameters until they're ready to deploy their payload. We've observed AI malware that mimics legitimate software behavior so precisely that it passes behavioral analysis checks while establishing persistent backdoors into target systems.
The Single Point of Failure
Perhaps the most critical weakness of traditional antivirus approaches is that they represent a single point of failure. If an attacker can bypass or disable the antivirus system, the entire network becomes vulnerable to compromise.
AI attackers specifically target security systems as part of their initial reconnaissance and attack strategy. They understand that disabling antivirus protection eliminates the primary barrier between them and their objectives.
Network Blindness
Traditional endpoint protection focuses on individual devices but provides limited visibility into network-wide attack patterns. AI threats often operate across multiple systems simultaneously, making network-level detection and response critical for effective defense.
A sophisticated AI attack might compromise a low-value workstation, use it to scan for other vulnerable systems, laterally move to high-value servers, and exfiltrate data through seemingly legitimate network traffic. Endpoint-only protection might detect individual components of this attack but miss the larger pattern that indicates a coordinated AI-powered campaign.
[IMAGE_HERE]
Defense in Depth: The Multi-Layered Approach That Stops AI Attacks
Defense in depth cybersecurity operates on the principle that no single security measure is perfect, but multiple overlapping layers of protection can detect, contain, and neutralize even sophisticated AI-powered threats. This approach recognizes that some attacks will penetrate outer defenses and prepares multiple fallback positions to prevent complete compromise.
Think of it like protecting a bank vault. You don't just rely on a single lock on the front door: you implement multiple barriers including perimeter security, access controls, motion detectors, cameras, and human guards. Each layer provides independent protection, and bypassing one layer doesn't automatically defeat the entire security system.
Layer 1: Perimeter Defense and Threat Intelligence
The first layer of defense focuses on preventing AI attackers from establishing initial footholds in your network. This includes:
Advanced firewalls that analyze traffic patterns and can identify AI reconnaissance attempts even when they're distributed across long time periods. Traditional firewalls look for known attack signatures, but AI-aware systems can detect subtle patterns that indicate automated reconnaissance.
Real-time threat intelligence feeds that provide information about emerging AI attack patterns and indicators of compromise. These feeds enable security systems to recognize and block new threats even before specific signatures are available.
Email security systems that can identify AI-generated phishing attempts by analyzing linguistic patterns, sender reputation, and behavioral indicators that human-generated emails typically don't exhibit.
DNS filtering that prevents communication with known malicious domains and can identify domain generation algorithms commonly used by AI malware to establish command and control communications.
Layer 2: Network Segmentation and Micro-Segmentation
Even if AI attackers penetrate perimeter defenses, network segmentation limits their ability to move laterally through your systems and access critical data.
VLAN configuration that isolates different types of network traffic and prevents unauthorized movement between network segments. Critical servers and databases are placed in protected network zones that require explicit authorization to access.
Zero-trust network architecture that treats every connection attempt as potentially hostile and requires authentication and authorization regardless of the source location. This approach prevents AI attackers from using compromised credentials to freely navigate through network resources.
Micro-segmentation that creates granular security zones around individual applications and data repositories. Even if an AI attacker gains access to one system, they cannot automatically access related systems without additional authentication.
Network access control (NAC) systems that continuously verify the identity and security posture of devices attempting to connect to network resources. Compromised devices can be automatically quarantined before they can be used as platforms for further attacks.
Layer 3: Endpoint Detection and Response (EDR)
While traditional antivirus focuses on preventing malware from executing, EDR systems monitor endpoint behavior and can detect and respond to threats that successfully establish footholds on individual devices.
Behavioral analysis engines that use machine learning to identify anomalous activity patterns that might indicate AI-powered attacks. These systems can detect subtle changes in system behavior that signature-based approaches typically miss.
Memory protection technologies that prevent AI malware from using advanced techniques like reflective DLL injection, process hollowing, and other methods commonly employed to evade traditional detection.
Automated response capabilities that can immediately isolate compromised endpoints, kill malicious processes, and prevent lateral movement without requiring human intervention. This rapid response is critical when facing AI attackers that can operate faster than human response times.
Forensic collection and analysis tools that preserve evidence of attack methods and help security teams understand how AI threats operate, enabling better defense strategies for future incidents.
Layer 4: Identity and Access Management
AI attackers often focus on compromising legitimate user credentials rather than exploiting technical vulnerabilities. Comprehensive identity protection addresses this attack vector through multiple mechanisms.
Multi-factor authentication (MFA) that requires multiple forms of identity verification for access to critical systems. Even if AI attackers obtain passwords through phishing or other methods, they cannot access protected resources without additional authentication factors.
Privileged access management (PAM) systems that tightly control administrative credentials and provide detailed auditing of all privileged activities. AI attackers specifically target administrative accounts because they provide broad access to organizational systems and data.
Identity behavioral analytics that establish baselines of normal user activity and can detect when accounts are being used by AI systems rather than legitimate users. These systems can identify subtle behavioral patterns that indicate automated rather than human activity.
Just-in-time access provisioning that grants elevated privileges only when needed and automatically revokes them after specific time periods. This approach minimizes the window of opportunity for AI attackers who might compromise privileged accounts.
Layer 5: Data Protection and Backup
The final layer of defense ensures that even if AI attackers successfully penetrate all other security measures, critical business data remains protected and recoverable.
Immutable backup systems that create tamper-proof copies of critical data that cannot be modified or deleted even by users with administrative privileges. AI ransomware specifically targets backup systems, making immutable protection essential.
Data loss prevention (DLP) technologies that monitor and control how sensitive information moves through organizational systems. These tools can detect when AI attackers attempt to exfiltrate large volumes of data or access information outside normal usage patterns.
Encryption at rest and in transit that ensures data remains protected even if AI attackers gain access to storage systems or intercept network communications. Advanced encryption systems use key management practices that prevent even sophisticated attackers from accessing protected information.
Continuous data integrity monitoring that can detect when AI attackers modify or corrupt data files. Early detection of data manipulation attempts enables rapid response before significant damage occurs.
[IMAGE_HERE]
Real-World Defense in Depth Success Stories
To illustrate the practical effectiveness of defense-in-depth cybersecurity against AI-powered threats, let's examine three recent cases where Connecticut businesses successfully defended against sophisticated attacks.
Case Study 1: The Manufacturing Company That Stopped a $500K Ransomware Attack
Precision Components Corp, a 120-employee manufacturing company in Waterbury, faced a coordinated AI ransomware attack in September 2024. The attack began with a spear-phishing email sent to their accounts payable clerk that appeared to come from a legitimate supplier requesting updated banking information.
The AI-generated email was sophisticated enough to pass through their standard email filters and convince the employee to click on a malicious link. However, the defense-in-depth strategy we had implemented for Precision Components created multiple opportunities to detect and stop the attack:
Layer 1 Detection: Although the initial phishing email bypassed email filters, the malicious payload it downloaded was detected by advanced threat intelligence systems that identified behavioral patterns associated with AI-generated malware.
Layer 2 Containment: When the malware attempted to scan the network for additional targets, network segmentation rules prevented it from accessing critical manufacturing systems and isolated it to the finance department subnet.
Layer 3 Response: Endpoint detection and response systems immediately flagged anomalous behavior on the infected workstation and automatically isolated it from the network before the AI could establish persistent access.
Layer 4 Protection: When the attack attempted to escalate privileges using compromised credentials, multi-factor authentication requirements prevented unauthorized access to administrative accounts.
Layer 5 Preservation: Throughout the incident, immutable backup systems continued protecting critical data, ensuring that even if the attack had succeeded, business operations could have continued with minimal disruption.
The entire attack was detected, contained, and neutralized within 12 minutes of the initial compromise. Precision Components experienced no data loss, no operational disruption, and no ransom payment. The contrast with their previous security posture: which relied primarily on traditional antivirus protection: was stark.
Case Study 2: The Healthcare Practice That Defeated Advanced Persistent Threats
Shoreline Medical Associates, a multi-specialty practice with four locations across Connecticut, discovered they were being targeted by an AI-powered advanced persistent threat (APT) that had been monitoring their systems for over six months.
The AI attacker had gained initial access through a compromised vendor portal and had been slowly expanding its foothold throughout the practice's network. The attack was discovered only when our security monitoring systems detected subtle anomalies in network traffic patterns that indicated automated data collection activities.
The Threat Profile: Analysis revealed that the AI system had been mapping patient databases, identifying high-value targets (including several prominent public figures), and preparing for a large-scale data exfiltration operation that would likely have resulted in HIPAA violations affecting thousands of patients.
Defense Response: The defense-in-depth strategy enabled a coordinated response that eliminated the threat while preserving evidence for law enforcement:
Network segmentation immediately contained the AI's access to previously compromised systems, preventing further lateral movement while security teams analyzed the extent of the breach.
Identity and access management systems revoked all potentially compromised credentials and required re-authentication for all users, effectively cutting off the AI's ability to maintain persistent access.
Endpoint detection and response tools identified and removed malicious payloads from infected systems while preserving forensic evidence about the AI's attack methods and capabilities.
Data protection measures confirmed that patient information had not been exfiltrated, and backup systems verified the integrity of all medical records throughout the organization.
Outcome: The sophisticated AI attack that had operated undetected for six months was completely eliminated within 48 hours of discovery. Shoreline Medical Associates avoided potential HIPAA fines exceeding $1 million and maintained patient trust through transparent communication about their security measures and incident response capabilities.
Case Study 3: The Financial Services Firm That Outsmarted AI Social Engineering
Capital Advisors Group, a wealth management firm in Greenwich managing over $200 million in client assets, faced a sophisticated AI social engineering campaign designed to compromise their client communication systems and gain access to sensitive financial information.
The AI attack combined multiple vectors including personalized phishing emails, voice deepfake technology, and social media manipulation to create a comprehensive campaign targeting the firm's senior partners and key support staff.
Attack Sophistication: The AI system had analyzed public records, social media profiles, and professional networking sites to create detailed psychological profiles of target employees. It then used this information to craft highly personalized attack messages that referenced specific client relationships, recent business developments, and personal information about the targets' families and interests.
Voice deepfake technology was used to create convincing phone calls that appeared to come from existing clients requesting urgent account changes or wire transfers. The AI-generated voices were sophisticated enough to fool voice recognition systems and included specific details about account holdings and investment strategies.
Layered Defense Response: The defense-in-depth strategy provided multiple opportunities to detect and counter the AI social engineering campaign:
Advanced email security systems identified linguistic patterns and metadata inconsistencies that indicated AI-generated phishing attempts, even when the content appeared highly personalized and legitimate.
Identity and access management protocols required multi-factor authentication for all account access and financial transactions, preventing unauthorized changes even if employees had been convinced to provide passwords.
Network monitoring systems detected communication patterns associated with social engineering campaigns and flagged suspicious contact attempts for further investigation.
Employee training programs focused on AI-powered social engineering threats enabled staff to recognize and report sophisticated manipulation attempts, creating a human intelligence layer that complemented technical defenses.
Results: Despite the sophistication of the AI social engineering campaign, Capital Advisors Group suffered no compromise of client data, no unauthorized financial transactions, and no regulatory violations. The firm's ability to defeat advanced AI attacks became a competitive advantage in client retention and new business development.
The Connecticut Business Advantage: Proactive Security Investment
Connecticut businesses that invest in defense-in-depth cybersecurity strategies gain significant competitive advantages beyond just improved security. In our increasingly interconnected economy, robust cybersecurity becomes a business enabler rather than just a defensive measure.
Regulatory Compliance Confidence
Connecticut businesses operating in regulated industries face increasingly stringent cybersecurity requirements. Healthcare practices must comply with HIPAA security rules, financial services firms face SEC cybersecurity regulations, and legal practices have ethical obligations to protect client confidentiality.
Defense-in-depth strategies provide the comprehensive documentation and technical controls required to demonstrate compliance with these various regulatory frameworks. Businesses with robust cybersecurity postures spend significantly less time and money on compliance audits and face lower risk of regulatory violations.
Client Trust and Business Development
Large corporations and government entities increasingly require their vendors and partners to demonstrate comprehensive cybersecurity capabilities before entering into business relationships. Businesses with defense-in-depth security strategies can differentiate themselves in competitive bidding processes and command premium pricing for their services.
Connecticut businesses that can provide detailed documentation of their cybersecurity measures, incident response capabilities, and threat detection systems often win contracts over competitors who cannot demonstrate equivalent protection.
Cyber Insurance Advantages
Insurance companies are becoming increasingly sophisticated in their evaluation of cybersecurity risks. Businesses with defense-in-depth security strategies typically qualify for lower premiums, higher coverage limits, and more favorable policy terms.
More importantly, businesses with comprehensive security measures are less likely to face coverage disputes when claims are filed. Insurance companies are more willing to pay claims when they can verify that businesses implemented reasonable security measures and followed industry best practices.
Operational Efficiency
While cybersecurity investments require upfront costs, defense-in-depth strategies often improve operational efficiency by reducing the time and resources required to manage security incidents, investigate potential threats, and recover from successful attacks.
Businesses with proactive security measures spend significantly less time dealing with malware infections, data recovery procedures, and incident response activities. This efficiency gain often offsets the cost of security investments within the first year of implementation.
[IMAGE_HERE]
Implementation Roadmap for Connecticut SMBs
Implementing defense-in-depth cybersecurity might seem overwhelming for Connecticut SMBs, but the key is to approach it systematically and prioritize the most critical protective measures first. Our Smart Paws security team has developed a proven implementation roadmap that enables businesses to build comprehensive protection while maintaining operational continuity.
Phase 1: Foundation Building (Month 1)
The first phase focuses on establishing basic security hygiene and addressing the most critical vulnerabilities that AI attackers commonly exploit.
Identity and Access Management: Implement multi-factor authentication for all user accounts, establish strong password policies, and deploy privileged access management for administrative functions. These measures prevent AI attackers from using compromised credentials to gain broad access to organizational systems.
Network Segmentation: Create basic VLAN configurations that isolate critical servers and databases from general user workstations. This fundamental segmentation limits the ability of AI attackers to move laterally through your network even if they successfully compromise individual endpoints.
Endpoint Protection: Deploy advanced endpoint detection and response solutions that can identify behavioral anomalies associated with AI-powered malware. These systems provide real-time monitoring and automated response capabilities that can neutralize threats faster than human response times.
Backup and Recovery: Implement immutable backup systems that protect critical data from ransomware attacks and provide rapid recovery capabilities. AI ransomware specifically targets backup systems, making tamper-proof protection essential.
Phase 2: Detection and Response (Month 2)
The second phase focuses on building comprehensive visibility into network activity and establishing rapid response capabilities.
Security Information and Event Management (SIEM): Deploy centralized logging and analysis systems that can correlate security events across multiple systems and identify patterns associated with AI-powered attacks. Modern SIEM systems use machine learning to detect subtle anomalies that might indicate sophisticated threats.
Network Monitoring: Implement comprehensive network traffic analysis that can identify unusual communication patterns, detect lateral movement attempts, and flag potential data exfiltration activities. AI attackers often operate through seemingly legitimate network traffic, making deep packet inspection critical.
Incident Response Planning: Develop detailed procedures for detecting, containing, and recovering from cyber attacks. Include specific protocols for AI-powered threats that might operate faster than traditional incident response timelines.
Security Awareness Training: Conduct comprehensive training programs that help employees recognize AI-powered social engineering attempts, phishing campaigns, and other human-targeted attack vectors. Regular training updates address emerging threat patterns and attack techniques.
Phase 3: Advanced Protection (Month 3)
The third phase implements sophisticated protection measures that provide defense against the most advanced AI-powered threats.
Zero Trust Architecture: Deploy comprehensive zero-trust networking that treats every connection attempt as potentially hostile and requires continuous verification of user and device identity. This approach prevents AI attackers from using compromised credentials to freely navigate through network resources.
Threat Intelligence Integration: Implement real-time threat intelligence feeds that provide information about emerging AI attack patterns and enable proactive blocking of known malicious indicators. Intelligence-driven defense helps security systems recognize and counter new threats before they successfully compromise organizational assets.
Advanced Data Protection: Deploy comprehensive data loss prevention systems that monitor and control how sensitive information moves through organizational systems. These tools can detect when AI attackers attempt to exfiltrate data or access information outside normal usage patterns.
Continuous Security Testing: Establish regular penetration testing and vulnerability assessment programs that specifically evaluate defenses against AI-powered attack techniques. Regular testing ensures that security measures remain effective against evolving threat landscapes.
Ongoing Management and Optimization
Defense-in-depth cybersecurity requires continuous monitoring, testing, and improvement to remain effective against evolving AI-powered threats. Successful implementation includes:
Regular Security Assessments: Quarterly evaluations of security posture that identify new vulnerabilities and assess the effectiveness of existing protective measures against current threat patterns.
Threat Hunting Activities: Proactive searches for indicators of compromise that might indicate AI attackers have established persistent access to organizational systems. Advanced threats often operate below the threshold of automated detection systems.
Security Metrics and Reporting: Comprehensive measurement of security program effectiveness including incident response times, detection rates, and business impact metrics. Regular reporting ensures that security investments align with business objectives and provide measurable value.
Technology Updates and Integration: Continuous evaluation and implementation of new security technologies that address emerging AI-powered threat techniques. The security technology landscape evolves rapidly, and defense systems must adapt to remain effective.
The Cost of Inaction vs. the Value of Protection
Connecticut SMBs often struggle with justifying cybersecurity investments, but the financial analysis strongly favors proactive security measures over reactive incident response. Our analysis of actual client experiences demonstrates that comprehensive defense-in-depth strategies provide significant return on investment.
Quantifying the Risk
Based on FoxPowerIT's experience with Connecticut businesses over the past three years, we've documented the following average costs associated with successful AI-powered cyber attacks:
Immediate Response Costs: $25,000-$75,000 for forensic investigation, incident containment, and system restoration. These costs occur regardless of whether the attack succeeds in its primary objectives.
Business Disruption: $50,000-$200,000 per week in lost productivity, delayed deliveries, and customer service issues. AI-powered attacks often cause extended outages because they're designed to maximize damage and complicate recovery efforts.
Data Recovery and Reconstruction: $100,000-$500,000 for rebuilding databases, recreating documents, and restoring operational systems from backup or manual records. AI attackers specifically target backup systems, making recovery significantly more expensive and time-consuming.
Regulatory and Legal Costs: $50,000-$1,000,000 in fines, legal fees, and compliance remediation depending on industry and the scope of compromised data. AI-powered attacks often result in larger-scale breaches that trigger more severe regulatory responses.
Reputation and Customer Loss: $100,000-$2,000,000 in long-term revenue impact from customer attrition, increased customer acquisition costs, and competitive disadvantage. Connecticut's business community is relatively small, and reputation damage spreads quickly through professional networks.
Insurance Impacts: Premium increases of 200-500% following successful cyber attacks, along with reduced coverage limits and higher deductibles. Some businesses become uninsurable after major incidents, creating ongoing risk exposure.
Investment in Protection
Comprehensive defense-in-depth cybersecurity typically costs Connecticut SMBs $500-$1,500 per employee per year, depending on business size, industry, and specific risk factors. For a typical 50-employee Connecticut business, annual security investment ranges from $25,000-$75,000.
This investment includes:
- Advanced threat protection systems
- Security monitoring and response services
- Employee training and awareness programs
- Regular security assessments and testing
- Incident response planning and preparation
- Compliance documentation and reporting
Return on Investment Analysis
Even preventing a single moderate cyber attack typically saves 3-10 times the annual cost of comprehensive security protection. Businesses that implement defense-in-depth strategies before experiencing major incidents achieve the following benefits:
Reduced Insurance Costs: Businesses with comprehensive cybersecurity measures typically qualify for 20-40% lower cyber insurance premiums and benefit from higher coverage limits and lower deductibles.
Competitive Advantage: Robust cybersecurity capabilities enable Connecticut businesses to pursue larger contracts and premium clients that require demonstrated security competence.
Operational Efficiency: Proactive security measures reduce the time and resources spent dealing with security incidents, malware infections, and recovery activities.
Regulatory Compliance: Comprehensive security programs streamline compliance audits and reduce the risk of regulatory violations that can result in significant fines and operational restrictions.
Business Continuity: Defense-in-depth strategies ensure that businesses can continue operating even when facing sophisticated AI-powered attacks that might completely disable competitors with basic security measures.
Your Next Steps: From Vulnerability to Victory
The battle between AI attackers and AI defenders is already underway, and Connecticut businesses that delay implementing comprehensive cybersecurity strategies are essentially conceding defeat before the fight begins. The good news is that defense-in-depth cybersecurity provides clear advantages over even sophisticated AI-powered attacks when properly implemented and maintained.
Immediate Action Items (This Week)
-
Security Assessment: Conduct a comprehensive evaluation of your current cybersecurity posture to identify critical vulnerabilities that AI attackers commonly exploit.
-
Incident Response Planning: Develop basic procedures for detecting and responding to cyber attacks, with specific consideration for AI-powered threats that operate faster than human response times.
-
Employee Awareness: Begin training programs that help your team recognize AI-generated phishing attempts, social engineering campaigns, and other human-targeted attack vectors.
Short-Term Implementation (This Month)
-
Multi-Factor Authentication: Deploy MFA for all user accounts and administrative functions to prevent AI attackers from using compromised credentials for broad network access.
-
Network Segmentation: Implement basic VLAN configurations that isolate critical systems and limit the ability of AI attackers to move laterally through your network.
-
Advanced Endpoint Protection: Replace basic antivirus software with comprehensive endpoint detection and response solutions that can identify behavioral patterns associated with AI-powered malware.
Strategic Implementation (This Quarter)
-
Comprehensive Defense Architecture: Work with cybersecurity professionals to design and implement a complete defense-in-depth strategy tailored to your business requirements and risk profile.
-
Security Monitoring and Response: Deploy centralized security monitoring systems that provide real-time visibility into network activity and automated response to detected threats.
-
Continuous Improvement Programs: Establish regular testing, assessment, and optimization procedures that ensure your security measures remain effective against evolving AI-powered threats.
The AI revolution in cybersecurity is not coming: it's already here. Connecticut businesses that recognize this reality and take proactive steps to implement comprehensive defense strategies will not only survive the coming wave of AI-powered attacks but will thrive in an environment where their competitors are struggling with basic security challenges.
At FoxPowerIT, our Smart Paws security team specializes in helping Connecticut SMBs implement enterprise-grade defense-in-depth cybersecurity strategies that provide comprehensive protection against both current and emerging AI-powered threats. We understand the unique challenges facing small and medium-sized businesses and have developed proven approaches that provide maximum security value within realistic budget constraints.
Don't wait until you're the next business owner explaining to clients, regulators, and stakeholders how an AI-powered attack compromised years of critical data while your traditional antivirus software sat helplessly on the sidelines. The technology exists today to build comprehensive protection against even the most sophisticated AI threats: the only question is whether you'll implement it before or after your first major attack.
The war between AI attackers and AI defenders will define cybersecurity for the next decade. Make sure your Connecticut business is fighting with the most advanced weapons available, not yesterday's tools in tomorrow's battles.
For comprehensive security management and firewall protection services designed specifically for Connecticut SMBs, contact our Smart Paws security team to discuss your defense-in-depth cybersecurity strategy.
VoIP Telephone Systems Just Got Scary Smart: 7 AI Features That Will Transform How Your Connecticut Business Communicates in 2025

Sarah Martinez, the operations manager at Hartford Medical Supply, was skeptical when she first heard about AI-powered VoIP systems. "We're a medical supply company, not a tech startup," she told our FoxPowerIT Smart Paws team. "We just need reliable phones that work when doctors call for emergency supplies."
Six months later, Sarah's perspective had completely changed. Her new AI-enhanced VoIP system had automatically transcribed and categorized over 1,200 customer service calls, identified patterns in emergency supply requests that helped optimize inventory, and even detected potential fraud attempts by analyzing voice patterns and call behaviors. Most impressively, the system had reduced average call resolution time by 40% while simultaneously improving customer satisfaction scores.
"I thought AI in phone systems was just marketing hype," Sarah reflected. "But now I can't imagine running our business without these capabilities. It's like having a super-intelligent assistant monitoring every conversation and helping our team make better decisions."
Sarah's experience represents a fundamental shift happening across Connecticut businesses in 2025. VoIP telephone systems have evolved far beyond simple digital voice transmission: they've become intelligent communication platforms that can understand, analyze, and enhance every aspect of business communication.
This isn't just about clearer phone calls or lower costs. The newest generation of AI-powered VoIP systems can predict customer needs, automate complex workflows, provide real-time coaching to employees, and deliver business insights that were previously impossible to obtain. For Connecticut SMBs that implement these technologies thoughtfully, the competitive advantages are substantial.
[IMAGE_HERE]
The Intelligence Revolution in Business Communication
Traditional phone systems were essentially digital versions of analog technology: they transmitted voice signals from one location to another with minimal processing or analysis. Modern AI-powered VoIP systems represent a completely different approach to business communication, treating every call as a data-rich interaction that can provide valuable insights and automation opportunities.
From Reactive to Predictive Communication
The most significant transformation is the shift from reactive to predictive communication capabilities. Instead of simply handling incoming calls, AI-powered systems can anticipate customer needs, route communications to the most appropriate resources, and even initiate proactive outreach based on behavioral patterns.
Consider a typical Connecticut accounting firm during tax season. Traditional phone systems would simply route incoming calls to available accountants, often creating bottlenecks and frustrated clients. An AI-powered VoIP system can analyze historical call patterns, identify which types of questions typically require specific expertise, and automatically route calls to the most qualified team members while simultaneously pulling relevant client information and tax documents to support the conversation.
Real-Time Intelligence and Decision Support
Modern VoIP systems don't just record conversations: they actively analyze them in real-time to provide immediate insights and support to both employees and managers. This capability transforms routine phone interactions into strategic business intelligence gathering opportunities.
During active calls, AI systems can provide real-time suggestions to sales representatives, flag potential compliance issues in regulated industries, and even detect emotional states that might indicate customer dissatisfaction or sales opportunities. This level of support enables even junior employees to deliver senior-level customer service and sales performance.
Automated Workflow Integration
Perhaps most powerfully, AI-powered VoIP systems can automatically trigger business processes based on conversation content and context. A customer service call about a defective product can automatically initiate a return merchandise authorization, update inventory systems, and generate quality control alerts: all without manual intervention.
This automation capability reduces administrative overhead, minimizes errors, and ensures that important business processes happen consistently and promptly regardless of individual employee knowledge or attention to detail.
The 7 Game-Changing AI Features Transforming Connecticut Businesses
Based on our experience implementing AI-powered VoIP systems for over 200 Connecticut businesses in the past year, we've identified seven specific features that consistently deliver transformational business value across industries and company sizes.
1. Real-Time Call Transcription and Sentiment Analysis
Modern AI systems can transcribe phone conversations in real-time with over 95% accuracy while simultaneously analyzing the emotional tone and sentiment of both participants. This capability provides immediate visibility into customer satisfaction, employee performance, and potential issues that might require management attention.
Practical Applications:
- Customer service managers receive instant alerts when calls become heated or customers express significant dissatisfaction
- Sales managers can identify deals at risk based on sentiment analysis of prospect conversations
- Compliance officers in regulated industries can flag conversations that might indicate policy violations or training needs
- HR departments can analyze employee phone interactions to identify coaching opportunities and performance improvements
Connecticut Success Story: Shoreline Insurance Agency implemented real-time sentiment analysis and discovered that 30% of their "routine" policy renewal calls actually involved frustrated customers with concerns about coverage or pricing. By identifying these issues during the calls rather than through post-call surveys, they were able to address problems immediately and improve their renewal rate by 15%.
2. Intelligent Call Routing and Skills-Based Distribution
AI-powered routing goes far beyond traditional "press 1 for sales" systems. These systems can analyze caller history, communication preferences, problem complexity, and even emotional state to route calls to the most appropriate team member with the relevant skills and availability.
Advanced Routing Capabilities:
- Natural language processing understands caller intent from free-form speech rather than menu selections
- Historical analysis identifies which team members have been most successful with similar customers or issues
- Real-time skills assessment considers current workload, expertise level, and performance metrics
- Predictive routing anticipates likely call outcomes and optimizes for desired business results
Connecticut Success Story: TechFlow Solutions, a software development company in Stamford, implemented AI-powered call routing and reduced average call resolution time from 18 minutes to 11 minutes while improving customer satisfaction scores by 25%. The system learned that certain types of technical support issues were resolved more quickly when routed to specific engineers based on their expertise and communication style.
3. Automated Call Summarization and Action Item Generation
After each call, AI systems can generate comprehensive summaries that capture key discussion points, decisions made, and required follow-up actions. These summaries are automatically integrated with CRM systems, project management tools, and other business applications.
Summary Capabilities Include:
- Extraction of key topics, decisions, and commitments from conversation transcripts
- Automatic identification of action items with suggested assignees and due dates
- Integration with existing business systems to update customer records and project status
- Generation of follow-up reminders and workflow triggers based on conversation content
Connecticut Success Story: Capital Advisors Group, a wealth management firm in Greenwich, uses automated call summarization to ensure that every client conversation is properly documented for compliance purposes. The system automatically generates meeting notes that satisfy SEC requirements while freeing financial advisors to focus on client relationships rather than administrative documentation.
4. Predictive Analytics and Customer Behavior Insights
AI systems can analyze patterns across thousands of phone interactions to identify trends, predict customer behaviors, and recommend proactive business actions. This capability transforms routine customer service data into strategic business intelligence.
Analytics Capabilities:
- Identification of customers likely to churn based on conversation patterns and sentiment trends
- Prediction of seasonal demand fluctuations based on inquiry patterns and historical data
- Detection of product issues or quality problems through analysis of support call content
- Recognition of sales opportunities through analysis of customer questions and interests
Connecticut Success Story: Precision Components Corp, a manufacturing company in Waterbury, uses predictive analytics to identify potential quality issues weeks before they would typically be discovered through formal quality control processes. By analyzing customer service calls for specific keywords and sentiment patterns, they can detect emerging problems and implement corrective measures before they impact major clients.
5. Real-Time Language Translation and Communication Assistance
Modern VoIP systems can provide real-time translation services that enable Connecticut businesses to serve customers who speak different languages without requiring multilingual staff. Beyond basic translation, these systems can also provide cultural communication guidance and industry-specific terminology support.
Translation Features:
- Real-time speech translation for over 40 languages with business-quality accuracy
- Text-to-speech capability that allows translated responses to be spoken naturally
- Cultural context awareness that adapts communication style for different cultural backgrounds
- Industry-specific terminology databases that ensure accurate translation of technical terms
Connecticut Success Story: Hartford Medical Supply expanded their service territory to include several predominantly Spanish-speaking communities after implementing real-time translation capabilities. They were able to serve these new markets without hiring additional bilingual staff, increasing their customer base by 20% within six months.
6. Voice Biometrics and Enhanced Security
AI-powered voice recognition provides sophisticated security capabilities that go beyond traditional password protection. These systems can verify caller identity through voice patterns, detect potential fraud attempts, and maintain comprehensive audit trails for compliance purposes.
Security Capabilities:
- Voice print authentication that verifies caller identity within seconds
- Fraud detection algorithms that identify suspicious calling patterns or voice anomalies
- Compliance recording with tamper-proof storage and automatic retention management
- Integration with existing security systems for comprehensive identity management
Connecticut Success Story: New Haven Community Bank implemented voice biometrics for telephone banking and reduced fraud losses by 80% while improving customer satisfaction through faster account access. Customers no longer need to remember complex security questions: their voice serves as both identification and authentication.
7. Intelligent Virtual Assistants and Automated Customer Service
Advanced AI virtual assistants can handle complex customer interactions that previously required human agents. These systems can access multiple business databases, make decisions within defined parameters, and escalate complex issues to human agents with complete context and relevant information.
Virtual Assistant Capabilities:
- Natural conversation flow that doesn't sound robotic or scripted
- Access to comprehensive business databases and customer history
- Ability to complete transactions, schedule appointments, and update account information
- Seamless escalation to human agents with complete conversation context
Connecticut Success Story: Waterbury HVAC Services implemented an AI virtual assistant that handles 60% of their after-hours service calls, scheduling emergency repairs, providing troubleshooting guidance, and managing routine maintenance appointments. The system reduced their need for after-hours human coverage while improving customer satisfaction through 24/7 availability.
[IMAGE_HERE]
Industry-Specific Applications Across Connecticut
The transformational impact of AI-powered VoIP systems varies significantly across different industries, but every sector we've worked with has found valuable applications that provide competitive advantages and operational improvements.
Healthcare and Medical Practices
Connecticut healthcare providers face unique communication challenges including HIPAA compliance, emergency response coordination, and complex patient scheduling requirements. AI-powered VoIP systems address these challenges while improving patient care and operational efficiency.
HIPAA-Compliant Communication: Advanced encryption and access controls ensure that all voice communications meet healthcare privacy requirements while providing comprehensive audit trails that satisfy regulatory documentation needs.
Emergency Response Optimization: AI systems can prioritize incoming calls based on urgency indicators, automatically route emergency calls to appropriate medical personnel, and maintain detailed logs of all emergency communications for quality assurance and legal protection.
Patient Care Coordination: Intelligent call routing ensures that patients are connected with appropriate healthcare providers based on their medical history, current treatments, and specific needs. Automated appointment scheduling integrates with practice management systems to optimize provider schedules and reduce patient wait times.
Shoreline Medical Associates serves over 15,000 patients across four Connecticut locations and implemented AI-powered VoIP to address communication challenges between locations and departments. Their system automatically routes calls based on patient history and provider availability, reducing average hold times by 70% and improving patient satisfaction scores significantly.
Legal Practices and Professional Services
Connecticut legal practices operate in a highly regulated environment where communication confidentiality, accurate documentation, and rapid response to client needs are critical for business success and ethical compliance.
Attorney-Client Privilege Protection: Advanced security features ensure that all client communications are properly protected and documented according to Connecticut bar requirements and ethical guidelines.
Conflict Checking Integration: AI systems can automatically check caller information against conflict databases to identify potential ethical issues before confidential information is disclosed.
Billable Time Optimization: Automated call tracking and categorization ensures that all client communications are properly documented for billing purposes while reducing administrative overhead for legal staff.
Hartford Legal Group represents clients across multiple practice areas and uses AI-powered VoIP to manage complex communication requirements. Their system automatically routes calls to attorneys based on practice area expertise and client relationships while maintaining comprehensive documentation for billing and conflict management purposes.
Financial Services and Banking
Connecticut financial services firms must balance customer accessibility with rigorous security requirements while maintaining compliance with multiple regulatory frameworks including SEC, FINRA, and state banking regulations.
Regulatory Compliance Recording: Automated recording and retention systems ensure that all required communications are properly documented and maintained according to regulatory requirements without requiring manual intervention.
Fraud Detection and Prevention: Voice biometrics and behavioral analysis can identify potential fraud attempts and suspicious activities during phone interactions, providing an additional security layer beyond traditional authentication methods.
Client Relationship Management: Integration with portfolio management and CRM systems provides financial advisors with complete client context during every interaction, enabling more personalized service and better investment advice.
Capital Management Partners manages over $150 million in client assets and implemented AI-powered communication systems to enhance client service while meeting strict compliance requirements. Their system automatically generates compliant records of all client interactions while providing advisors with real-time access to portfolio information and market data during conversations.
Manufacturing and Distribution
Connecticut manufacturing companies often manage complex supply chains, emergency repair services, and technical support requirements that benefit significantly from intelligent communication systems.
Supply Chain Coordination: AI systems can prioritize supplier communications based on production schedules, inventory levels, and delivery requirements while automatically documenting all interactions for quality and compliance purposes.
Technical Support Optimization: Intelligent routing connects customers with technical experts based on product knowledge, problem complexity, and historical resolution success rates.
Emergency Response Management: Critical production issues and equipment failures require immediate expert attention, and AI systems can automatically escalate these calls while providing technicians with relevant equipment history and troubleshooting resources.
Connecticut Precision Manufacturing produces components for aerospace and medical device companies and uses AI-powered VoIP to manage technical support for over 200 manufacturing clients. Their system automatically routes calls to technicians based on equipment expertise and provides real-time access to maintenance records and technical documentation during support calls.
[IMAGE_HERE]
Implementation Strategy for Connecticut SMBs
Successfully implementing AI-powered VoIP systems requires careful planning and strategic thinking, but the process doesn't need to be overwhelming for Connecticut small and medium-sized businesses. Our Smart Paws team has developed a proven approach that minimizes disruption while maximizing the business benefits of advanced communication technology.
Phase 1: Assessment and Planning (Week 1-2)
Current System Analysis: Document your existing communication infrastructure, identify pain points and inefficiencies, and quantify the business impact of communication-related problems. This analysis provides the baseline for measuring improvement and helps prioritize which AI features will provide the greatest value.
Business Process Mapping: Understanding how communication integrates with your existing business processes is critical for effective AI implementation. Map the flow of information from initial customer contact through order fulfillment, support resolution, or service delivery to identify automation opportunities.
Integration Requirements: Modern AI-powered VoIP systems need to integrate with your existing business applications including CRM systems, accounting software, project management tools, and industry-specific applications. Early identification of integration requirements prevents implementation delays and ensures maximum system value.
Connecticut Regulatory Considerations: Different industries have specific communication requirements that must be addressed during system design. Healthcare practices need HIPAA compliance, financial services require SEC documentation, and legal practices must maintain attorney-client privilege protections.
Phase 2: System Design and Configuration (Week 3-4)
Call Flow Design: Create intelligent call routing strategies that optimize customer experience while maximizing operational efficiency. This includes designing natural language prompts, skills-based routing rules, and escalation procedures that reflect your business priorities.
AI Feature Selection: Not every business needs every AI feature, and implementation is most successful when focused on capabilities that address specific business challenges. Prioritize features based on potential ROI and alignment with your operational goals.
Security and Compliance Configuration: Implement appropriate security measures including encryption, access controls, and audit logging that meet your industry requirements and protect sensitive business information.
Integration Development: Configure connections between your new VoIP system and existing business applications to ensure seamless information flow and process automation.
Phase 3: Deployment and Training (Week 5-6)
Phased Rollout: Rather than switching all communication to the new system simultaneously, implement AI-powered VoIP in phases that minimize business disruption while allowing for testing and refinement.
Employee Training: Success with AI-powered communication systems requires that employees understand how to leverage new capabilities effectively. Training should focus on practical applications rather than technical details and should be ongoing as system capabilities expand.
Performance Monitoring: Establish metrics and monitoring procedures that track system performance, user adoption, and business impact. Early identification of issues or optimization opportunities ensures continued system effectiveness.
Continuous Optimization: AI systems improve over time through machine learning, but they also benefit from ongoing configuration refinement based on actual usage patterns and business feedback.
Phase 4: Advanced Feature Implementation (Month 2-3)
Analytics and Reporting: Once basic system operation is stable, implement advanced analytics capabilities that provide business intelligence and operational insights from communication data.
Workflow Automation: Develop automated processes that trigger based on call content, customer information, or business rules to reduce administrative overhead and improve consistency.
Advanced Integration: Implement sophisticated integrations with specialized business applications that provide comprehensive workflow automation and information management.
Predictive Capabilities: Configure predictive analytics features that anticipate customer needs, identify business opportunities, and optimize resource allocation based on communication patterns.
Cost-Benefit Analysis and ROI Expectations
Connecticut businesses considering AI-powered VoIP systems often struggle with justifying the investment, particularly when existing phone systems appear to be functioning adequately. However, our analysis of actual client implementations demonstrates that the business benefits typically exceed the technology costs within 6-12 months.
Investment Considerations
Modern AI-powered VoIP systems typically cost 20-40% more than traditional business phone systems, but they also eliminate many separate technology expenses that businesses would otherwise need to purchase independently:
Traditional Communication Costs: Phone service, long-distance charges, maintenance contracts, and hardware replacement costs are typically reduced by 30-50% with comprehensive VoIP implementations.
Separate Software Licensing: AI-powered VoIP systems often include capabilities that would otherwise require separate software purchases including call recording, customer analytics, help desk management, and workflow automation tools.
Administrative Overhead: Automated features reduce the time employees spend on routine communication tasks including message transcription, call documentation, appointment scheduling, and customer information management.
Training and Support: Modern systems are designed for ease of use and typically require less employee training than traditional PBX systems while providing superior technical support through cloud-based management.
Quantifiable Business Benefits
Based on our experience with Connecticut SMBs, businesses typically achieve the following measurable benefits within the first year of AI-powered VoIP implementation:
Productivity Improvements: Average increase of 15-25% in employee productivity related to communication tasks, primarily through reduced administrative overhead and improved information access.
Customer Satisfaction: Typical improvement of 20-35% in customer satisfaction scores related to phone interactions, driven by reduced wait times, better call routing, and improved issue resolution capabilities.
Sales Performance: 10-20% improvement in sales conversion rates through better lead qualification, automated follow-up processes, and sales coaching capabilities provided by AI analysis.
**

