Picture this: It's Monday morning, and you're sipping your coffee when your phone starts buzzing. Your office manager is calling in a panic: your company's computers are locked up, and there's a message demanding $50,000 in Bitcoin. Your first thought? "But we have antivirus software!"
Here's the harsh reality hitting Connecticut businesses right now: having just antivirus protection in 2025 is like bringing a knife to a gunfight. While you're relying on that single layer of defense, cybercriminals are using sophisticated, multi-vector attacks that slip past traditional security like it's not even there.
That's where Defense in Depth comes in: and if you've never heard of it, you're not alone. Most Connecticut SMBs are flying blind when it comes to this critical cybersecurity strategy, and it's costing them everything.
What is Defense in Depth (And Why Should You Care)?
Defense in Depth isn't just another tech buzzword your IT guy throws around. It's a cybersecurity strategy that uses multiple layers of security controls throughout your IT system to provide redundancy when one defense fails or a vulnerability is exploited.
Think of it like this: imagine your business data is a treasure chest buried in your office. A single-layer security approach is like putting one lock on your front door and calling it a day. Defense in Depth? That's like having a security guard at the gate, cameras around the perimeter, locked doors throughout the building, a safe in your office, and the treasure chest itself having multiple locks.
The concept was originally developed by the National Security Agency (NSA) as a comprehensive approach to information and electronic security. The fundamental principle is simple: no single security measure is perfect, so you need overlapping defenses to create a resilient security posture.
But here's what's really wild: this isn't some cutting-edge concept that just emerged. Defense in Depth has been around for decades, yet the majority of Connecticut small and medium businesses are still operating like it's 1995.

The Brutal Connecticut Reality Check
Let me hit you with some numbers that should make every business owner in Connecticut lose sleep:
73% of small businesses in Connecticut experience some form of cyber attack within their first six months of operation. Read that again. Nearly three out of four businesses get hit before they even have a chance to get their feet under them.
But here's the kicker: it's not because these businesses have zero security. Most of them do have some protection. The problem is they're implementing incomplete, single-layer defenses that modern attackers bypass as easily as walking through an unlocked door.
Here's what's happening: Your typical IT service provider sells you a basic firewall and backup solution for around $2,000, slaps an "antivirus" sticker on your computers, and tells you you're "protected." Six months later, you're part of that 73% statistic, wondering how the hell this happened when you "did everything right."
The truth is, you didn't do everything right. You did the bare minimum, and in today's threat landscape, the bare minimum is basically worthless.
Why Connecticut SMBs Keep Getting It Wrong
The issue isn't that Connecticut business owners are stupid or careless. The problem is much deeper than that.
Problem #1: The Knowledge Gap
Most IT service providers in Connecticut don't actually understand Defense in Depth themselves. Installing a firewall is straightforward: any tech with a few months of experience can do it. But designing an integrated security architecture with network segmentation, endpoint detection and response, and security information and event management? That requires specialized knowledge that goes well beyond general IT support.
Problem #2: The Cost Illusion
Business owners see a $2,000 "security solution" and think they're covered. Meanwhile, they're spending $5,000 a month on coffee and office supplies without blinking. The problem isn't the cost: it's the perception of value. When you don't understand what comprehensive security looks like, cheap solutions seem adequate.
Problem #3: The "It Won't Happen to Me" Mentality
This one kills me. I've had business owners tell me, "We're just a small accounting firm: nobody cares about our data." Really? You're handling sensitive financial information for dozens of clients, but somehow you think you're not a target?
Here's a news flash: Small businesses are specifically targeted BECAUSE they have weak security. You're not flying under the radar: you're painting a bullseye on your back.
Problem #4: Confidence in the Wrong Places
Another devastating statistic: 73% of SMBs are not fully confident in their current managed service provider's ability to defend them against attacks. Think about that: nearly three-quarters of businesses don't trust their IT provider to protect them, but they're not doing anything about it.
Why? Because making a change feels risky and complicated. So they stick with inadequate protection and hope for the best.

The Financial Reality Nobody Talks About
Let's talk money for a minute, because that's what this really comes down to.
The average cost of implementing comprehensive Defense in Depth for a Connecticut SMB with 20-50 employees ranges from $15,000 to $35,000 in initial setup costs, with ongoing monthly costs of $2,000 to $5,000.
Before you start hyperventilating about those numbers, let me put this in perspective:
- The average cost of a successful cyberattack on a Connecticut small business is $254,445
- 60% of businesses that suffer a significant cyber attack close permanently within six months
- Your business insurance probably won't cover the full cost of a breach (and definitely won't cover lost reputation and customers)
From a pure return on investment perspective, spending $50,000 per year on comprehensive cybersecurity to protect against a single incident that could cost $250,000 and potentially destroy your business is one of the best investments you can make.
But it gets even better. Customers, partners, and vendors increasingly require proof of robust cybersecurity practices before doing business. Insurance companies are starting to require specific cybersecurity measures before providing coverage. Having proper Defense in Depth isn't just about protection anymore: it's about being able to compete and operate in the modern business environment.
The Simple 3-Layer Fix That Actually Works
Here's the good news: Defense in Depth doesn't have to be overwhelmingly complicated. You can think of it in three overarching layers that work together to create comprehensive protection.
Layer 1: Physical Controls
Physical controls are anything that physically limits or prevents access to IT systems. This includes fences, guards, dogs, CCTV systems, locked server rooms, and badge access systems.
Now, I know what you're thinking: "We're a small business: we don't need armed guards!" You're right, but you'd be amazed how many businesses overlook basic physical security.
What this looks like for a typical Connecticut SMB:
- Server equipment locked in a dedicated room or secure closet
- Security cameras covering entry points
- Badge or key card access to sensitive areas
- Visitor access controls and logging
- Secure disposal of sensitive documents and old equipment
The goal isn't to create Fort Knox: it's to ensure that an attacker who gains physical access to your building can't just walk up to a server and plug in a USB drive.
Real-world example: One of our clients had an employee who got fired on a Friday. That weekend, he came back with a key he'd copied months earlier, walked into the server room, and downloaded client data onto a USB drive. A $300 lock and a simple access control policy would have prevented a $50,000 lawsuit.
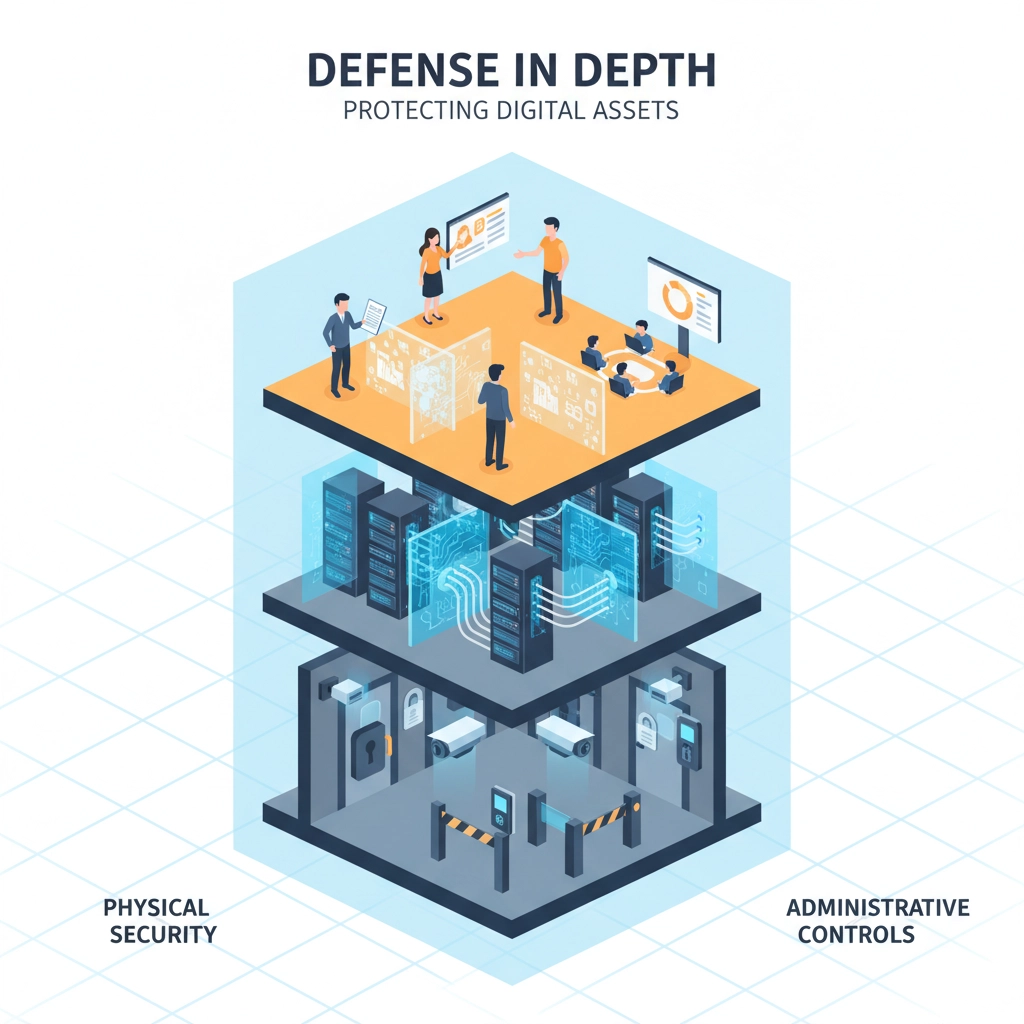
Layer 2: Technical Controls
This is where most businesses think cybersecurity begins and ends, but it's really just the middle layer. Technical controls are hardware or software designed to protect systems and resources.
Data Security:
- Encryption of data at rest and in transit
- Secure password policies and password managers
- Multi-factor authentication on all critical systems
- Regular automated backups with offline storage
Application Security:
- Web application firewalls
- Secure coding practices for any custom applications
- Regular security updates and patch management
- Application whitelisting on critical systems
Host Security:
- Endpoint detection and response (EDR) on all devices
- Vulnerability scanning and management
- System hardening and configuration management
- Mobile device management for company devices
Network Security:
- Next-generation firewalls with deep packet inspection
- Intrusion detection and prevention systems
- Network segmentation to isolate critical systems
- Virtual private networks (VPN) for remote access
- Comprehensive network monitoring and logging
The key principle here is redundancy: if an attacker penetrates your system at one level, a defense should exist at another level to catch them.
Real-world example: A ransomware attack hit one of our client's workstations through a phishing email. The endpoint detection caught the malicious activity, the network segmentation prevented it from spreading to servers, and the automated backup system meant they were back up and running in two hours instead of paying a ransom.
Layer 3: Administrative and Operational Controls
This is the layer most businesses completely ignore, and it's often the most important one. Administrative controls are your organization's policies and procedures governing how people interact with technology.
People Controls:
- Comprehensive security awareness training (not just a one-time video)
- Multi-factor authentication training and enforcement
- Clear policies for password creation and management
- Social engineering awareness and testing
- Regular security training updates and phishing simulations
Technology Controls:
- Formal patch management procedures with testing
- Regular risk assessments and vulnerability testing
- Information security policies that people actually follow
- Vendor security assessments for third-party services
- Data classification and handling procedures
Operations Controls:
- Principle of least privilege (people only get access to what they need)
- Regular access reviews and user account audits
- Detailed incident response procedures
- Business continuity and disaster recovery planning
- Regular security policy reviews and updates
Real-world example: We had a client where an employee received a phone call from someone claiming to be from their bank, asking them to verify their login credentials for a "security update." The employee had been through our social engineering training just two months earlier and recognized the scam immediately. That training saved them from a wire transfer fraud attempt worth $75,000.
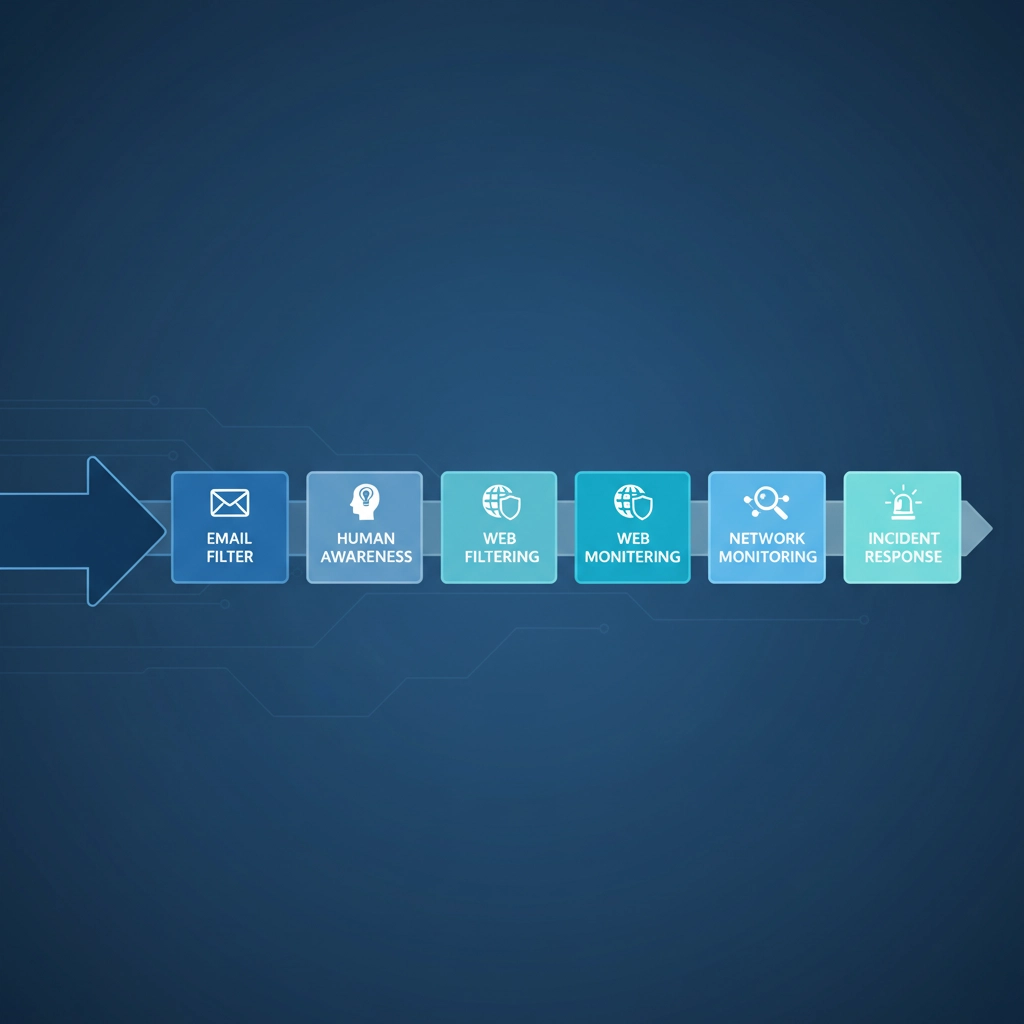
Why This Approach Actually Works
The Defense in Depth strategy works because it addresses the reality that every security control can fail. Modern cyber attacks are sophisticated, multi-stage operations that probe for weaknesses across multiple vectors.
Let me give you a real example of how a layered defense stopped an attack:
An attacker sent a targeted phishing email to one of our client's employees. The email looked like it came from their bank and included a link to "verify their account."
- Layer 1 (Technical): The email security gateway flagged the email as suspicious but didn't block it entirely (it was a very sophisticated fake)
- Layer 2 (Administrative): The employee had been through recent security awareness training and recognized the signs of a phishing attempt
- Layer 3 (Technical): Even if the employee had clicked the link, our web filtering would have blocked access to the malicious site
- Layer 4 (Technical): Even if they'd somehow reached the fake site and entered credentials, our network monitoring would have detected the unusual outbound connection
- Layer 5 (Administrative): Our incident response procedures meant the IT team would have been alerted immediately to investigate
The attack was stopped at Layer 2, but four additional layers were ready to catch it if it had gotten through. That's the power of Defense in Depth.
The Hidden Costs of Doing Nothing
Let's talk about what happens when you don't implement proper Defense in Depth, because the numbers are staggering:
Direct Financial Impact:
- Average breach cost: $254,445 for SMBs
- Legal fees and regulatory fines
- Notification costs (you have to tell everyone whose data was compromised)
- Credit monitoring services for affected customers
- Forensic investigation costs
Indirect Business Impact:
- Lost productivity during incident response and recovery
- Customer churn (people don't trust businesses that get breached)
- Reputation damage that lasts for years
- Increased insurance premiums
- Difficulty obtaining financing or investment
Regulatory Consequences:
- HIPAA fines for healthcare-related businesses
- State privacy law violations
- Industry-specific compliance failures
- Potential criminal liability for executives
The Ultimate Cost:
60% of small businesses that suffer a significant cyber attack close permanently within six months. That's not just losing money: that's losing everything you've built.
Making Defense in Depth Work for Your Business
The good news is that you don't have to implement everything at once. Here's how to approach this strategically:
Phase 1: Assessment and Quick Wins (Month 1-2)
- Conduct a comprehensive security assessment
- Implement multi-factor authentication on all critical systems
- Ensure all software is updated and patched
- Begin security awareness training for all employees
Phase 2: Technical Foundation (Month 3-4)
- Deploy endpoint detection and response on all devices
- Implement network segmentation
- Set up comprehensive backup and recovery systems
- Deploy next-generation firewall with proper configuration
Phase 3: Advanced Protection (Month 5-6)
- Implement security information and event management (SIEM)
- Deploy additional network monitoring and intrusion detection
- Conduct penetration testing and vulnerability assessments
- Develop and test incident response procedures
Phase 4: Continuous Improvement (Ongoing)
- Regular security training and phishing simulations
- Quarterly security assessments and updates
- Annual penetration testing
- Ongoing threat intelligence and security monitoring
The key is working with an IT partner who understands Defense in Depth strategy and can implement it properly. If your current IT provider can't explain these concepts or provide a comprehensive security roadmap, it's time for a change.
The Bottom Line
Defense in Depth isn't just about technology: it's about survival in the modern business environment. The businesses that understand this and implement proper layered security are the ones that will still be around in five years.
The businesses that keep thinking their basic antivirus and firewall are "good enough"? They're going to become cautionary tales.
The choice is yours: spend a reasonable amount on comprehensive protection now, or risk losing everything when the inevitable attack succeeds.
Your business, your employees, and your customers are counting on you to make the right choice.
Don't be part of the 73% that learns this lesson the hard way.
If you're ready to implement proper Defense in Depth security for your Connecticut business, contact our security management team for a comprehensive assessment. We'll show you exactly where your current security falls short and create a roadmap to proper protection that fits your budget and timeline.
Because the best time to implement Defense in Depth was five years ago. The second-best time is right now.

