
Picture this: You're reviewing your monthly expenses when you spot it: a cloud bill that's nearly triple what you expected. Your heart sinks as you realize those "quick deployments" and "temporary instances" have been quietly draining your budget for months.
You're not alone. Cloud spending is surging across all business sizes, with expectations of a 21.5% increase in 2025 compared to 2024 globally. Many small and medium-sized businesses find themselves allocating massive portions of their IT budgets to cloud services: 39% now spend up to $600,000 annually on public cloud alone.
The cloud promises flexibility, scalability, and enterprise-grade tools. But without proper management, it becomes a financial black hole that swallows budgets whole. The good news? With the right strategies, you can transform cloud costs from a business risk into a competitive advantage.

Why Cloud Costs Spiral Out of Control
Before diving into solutions, let's understand why cloud bills get so out of hand:
Overprovisioning Resources
Most businesses start by overestimating their needs. They provision large instances "just in case," then forget to scale down when actual usage proves much lighter. It's like renting a mansion when you only need a studio apartment.
Forgetting Unused Instances
Development environments, test servers, and temporary projects often outlive their purpose. These "zombie resources" continue consuming budget long after their usefulness expires.
Misunderstanding Pricing Models
Cloud pricing can be complex, with different rates for compute, storage, data transfer, and dozens of additional services. Without clear understanding, costs accumulate in unexpected ways.
Lack of Monitoring and Alerts
Many businesses operate blind: no spending alerts, no usage tracking, no regular audits. They only discover problems when the bill arrives.
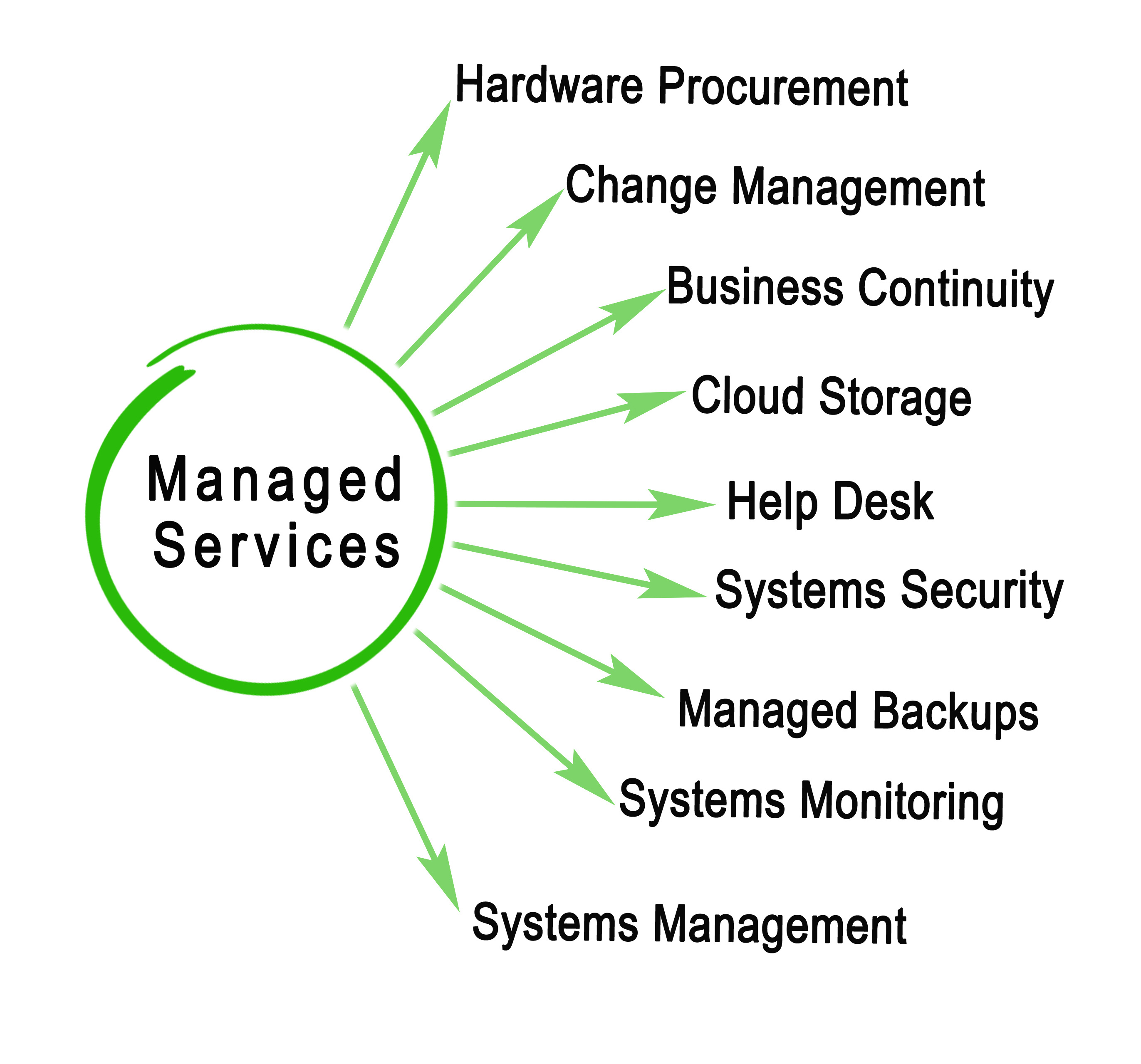
Strategic Cost Optimization Approaches
Right-Size Your Resources
Start by analyzing actual usage patterns versus provisioned capacity. Most applications use far less CPU and memory than initially allocated. Tools like AWS CloudWatch or Azure Monitor provide detailed metrics showing real utilization.
The key is starting small and scaling up based on demand rather than guessing upfront. You can always add more resources: it's much harder to recover overspent budget.
Implement Automated Scaling
Instead of running fixed-size resources 24/7, configure auto-scaling that adjusts capacity based on actual demand. During low-traffic periods, your infrastructure automatically scales down, reducing costs. When traffic spikes, it scales up to maintain performance.
This approach is particularly powerful for businesses with predictable patterns: like e-commerce sites that see higher traffic during business hours but little activity overnight.
Leverage Reserved and Spot Instances
For predictable workloads, reserved instances offer substantial discounts: sometimes 40-60% off on-demand pricing. If you know you'll need certain resources for a year or more, reservations provide guaranteed savings.
Spot instances work differently, offering unused cloud capacity at steep discounts. While they can be interrupted, they're perfect for batch processing, development environments, or any workload that can tolerate brief interruptions.
Optimize Storage Strategies
Not all data needs expensive, high-performance storage. Implement tiered storage that automatically moves infrequently accessed data to cheaper storage classes. Most cloud providers offer lifecycle policies that handle these transitions automatically.
Archive old backups, logs, and documents to long-term storage options that cost a fraction of standard storage rates. The key is matching storage performance to actual access patterns.
Eliminate Waste Through Monitoring
Set Up Cost Alerts
Configure spending alerts at multiple thresholds: maybe 50%, 75%, and 90% of your monthly budget. This provides early warning before costs spiral beyond control. Most cloud providers offer native alerting tools that can notify you via email, SMS, or integration with business communication platforms.
Regular Resource Audits
Schedule monthly reviews to identify unused resources, oversized instances, and unnecessary services. Create a checklist that covers:
- Unused elastic IP addresses
- Unattached storage volumes
- Idle load balancers
- Forgotten development environments
Track Resource Utilization
Use monitoring tools to identify consistently underutilized resources. If a server runs at 10% CPU utilization for weeks, it's likely oversized. If a database receives minimal queries, consider consolidating with other systems.

Tool Consolidation and Vendor Management
Many small businesses accumulate multiple optimization tools that provide overlapping functionality, creating redundant expenses without proportional value. Audit your current toolset to identify which provide unique benefits versus which duplicate capabilities.
Start by mapping all your cloud management tools: cost monitoring, security scanning, backup solutions, automation platforms. Look for areas where single tools can replace multiple subscriptions. Consolidation often reduces complexity while cutting costs.
Negotiation and Contract Optimization
As your cloud usage grows, don't accept standard pricing. Most providers offer volume discounts, especially for businesses committing to specific spending levels. Even small businesses can often negotiate better rates by demonstrating consistent usage patterns and growth projections.
Review contracts annually and compare pricing across providers. Cloud pricing changes frequently, and what was competitive last year might be expensive today.
Building Cost-Conscious Culture
Implement Governance Policies
Establish clear policies about who can provision resources and for what purposes. Require approval for instances above certain sizes or costs. Tag all resources with owner, project, and purpose information to maintain accountability.
Developer Training
Train your team to understand cloud costs and make cost-conscious decisions. Developers who understand pricing implications naturally make better architectural choices. Simple awareness often prevents the most expensive mistakes.
Regular Team Reviews
Include cloud costs in regular team meetings. When everyone sees the numbers, they become more mindful of resource usage. Celebrate cost optimization wins alongside performance improvements.
Automation for Sustainable Savings
Scheduled Shutdowns
Implement automated schedules that shut down non-production environments during off-hours. Development and testing environments rarely need to run nights and weekends, offering immediate 65-70% savings on those resources.
Resource Lifecycle Management
Automate resource deletion based on tags or age. For example, automatically delete untagged resources after 30 days or remove development environments older than 90 days. This prevents resource accumulation while maintaining necessary flexibility.
Partner with Experts
Managing cloud costs effectively requires constant attention and evolving expertise. Many businesses find value in working with managed IT service providers who specialize in cloud optimization.
Expert partners bring several advantages:
- Continuous monitoring and optimization
- Deep knowledge of pricing models and cost-saving opportunities
- Automated tools and processes for ongoing management
- Objective analysis of your cloud architecture and spending patterns
The right partnership can turn cloud cost management from a time-consuming burden into a strategic advantage that frees your team to focus on core business activities.
Your Next Steps
Start with a comprehensive audit of your current cloud usage and spending. Identify the biggest cost drivers and lowest-hanging fruit for optimization. Implement monitoring and alerts to prevent future surprises.
Remember: effective cloud cost optimization isn't about spending less: it's about spending smarter. Every dollar saved on unnecessary resources is a dollar available for growth, innovation, and competitive advantage.
The cloud should empower your business, not constrain it. With proper optimization strategies, you can maintain the flexibility and scalability that drew you to the cloud while keeping costs firmly under control.
From Offer Letter to First Login: How IT Makes New Hire Setup Easy

Sarah's first day at her new job should have been exciting. Instead, she spent three hours waiting for IT credentials, another hour figuring out which applications she needed, and the rest of the day trying to access systems that hadn't been properly configured for her role.
Sound familiar? According to Gallup, only 12% of employees strongly feel their company performs an excellent job onboarding new employees. That means 88% of businesses are essentially winging it when it comes to first impressions: and your IT setup is often the first real interaction a new hire has with your company's operational competence.
Poor IT onboarding doesn't just frustrate employees. It costs money, reduces productivity, and signals to new talent that your organization might not have its act together. But with the right processes, you can flip this scenario entirely.

The Hidden Costs of Poor IT Onboarding
When new employees can't access systems on day one, the ripple effects extend far beyond initial frustration:
Lost Productivity
Every hour a new hire spends waiting for access or troubleshooting login issues is an hour they're not contributing value. For professional roles, this can translate to hundreds of dollars in lost productivity per day.
Bad First Impressions
Your onboarding experience sets expectations for everything else. If basic IT systems aren't ready, new employees naturally wonder what other areas might be disorganized.
HR and IT Resource Drain
When onboarding is manual and reactive, your HR team spends excessive time coordinating with IT, and your IT team gets pulled into urgent, last-minute requests instead of focusing on strategic initiatives.
Security Vulnerabilities
Rushed account creation often leads to shortcuts: excessive permissions, weak password policies, or temporary access that never gets properly reviewed.
What Strategic IT Onboarding Looks Like
Pre-boarding: Setting the Foundation
The best onboarding experiences begin before the employee's first day. Once the offer letter is signed, your IT processes should automatically trigger:
- Email account creation with proper naming conventions
- Hardware ordering and configuration based on role requirements
- Software license assignment and application access provisioning
- Security training materials preparation and scheduling
This pre-boarding phase ensures everything is ready when your new hire walks through the door (or logs in remotely).
Automated Provisioning Systems
Manual account creation is time-intensive and error-prone. Modern IT departments use automated provisioning that creates all necessary accounts based on role templates. When HR enters a new employee into the system, it automatically:
- Generates accounts across all necessary platforms
- Assigns appropriate security groups and permissions
- Configures email signatures and distribution lists
- Sets up multi-factor authentication
- Schedules mandatory security and compliance training
Role-Based Access Templates
Instead of figuring out permissions individually for each hire, develop standardized access templates for common roles. A sales representative template might include CRM access, email marketing tools, and customer support systems, while a developer template provides code repositories, development environments, and deployment tools.
These templates ensure consistency, reduce setup time, and minimize security risks from excessive permissions.
Hardware and Software Coordination
Device Preparation and Configuration
New employee devices should be fully configured and ready for immediate use. This includes:
- Operating system updates and security patches
- Essential software installation and licensing
- VPN configuration for remote access
- Security tools and endpoint protection
- Company-specific applications and tools
For remote employees, consider shipping pre-configured devices directly to their home address, arriving the day before their start date.
Digital Asset Management
Maintain clear inventory tracking for all devices and software licenses. When someone starts, you should immediately know what hardware is assigned to them, what software they can access, and when licenses need renewal.
This tracking becomes crucial when employees eventually leave: you'll need to recover devices, revoke access, and reassign licenses efficiently.
Security Integration from Day One
Multi-Factor Authentication Setup
Security shouldn't be an afterthought in onboarding. Configure MFA during the initial setup process, ensuring new employees can't access company systems without proper authentication.
Provide clear instructions and support for MFA setup, including backup codes and alternative authentication methods.
Compliance Training and Acknowledgment
Different roles require different security awareness levels. Sales teams need to understand data privacy regulations, while developers need secure coding practices training.
Integrate required compliance training directly into the onboarding workflow, tracking completion and ensuring employees can't access sensitive systems until training is complete.

Communication and Support Systems
Clear Documentation and Resources
Create easily accessible documentation covering:
- Login procedures for all systems
- Password reset processes
- Help desk contact information
- Common troubleshooting steps
- Security policies and best practices
Make this information available in multiple formats: online knowledge base, PDF guides, and quick reference cards.
Dedicated IT Support During First Week
Assign specific IT support resources for new employee questions during their first week. This might be a dedicated help desk queue, specific contact person, or scheduled check-in calls.
New employees often hesitate to ask questions, assuming they should figure things out independently. Proactive support prevents small issues from becoming major frustrations.
Quality Assurance and Continuous Improvement
Testing and Validation Processes
Before any new hire arrives, test their account access across all required systems. Have someone from your team walk through the entire login process, verifying that permissions work correctly and systems respond as expected.
This testing catches configuration errors before they impact the employee experience.
Feedback Collection and Analysis
Regularly survey new employees about their IT onboarding experience. Ask specific questions about:
- How long it took to access required systems
- What systems or processes caused confusion
- What additional training or documentation would have been helpful
- Overall satisfaction with the technical setup process
Use this feedback to continuously refine and improve your onboarding procedures.
Measuring Success
Key Performance Indicators
Track metrics that matter:
- Time from start date to full system access
- Number of IT support tickets per new employee in first week
- New employee satisfaction scores for IT onboarding
- Percentage of employees fully productive by end of first week
Return on Investment
Calculate the value of streamlined onboarding by measuring:
- Reduced IT support time per new hire
- Faster time to productivity for new employees
- Decreased security incidents related to account setup errors
- Improved employee satisfaction and retention rates
Technology Tools That Make It Possible
Identity and Access Management (IAM) Systems
Modern IAM platforms automate much of the account creation and permission assignment process. They integrate with HR systems to trigger workflows automatically and provide centralized management for all user accounts.
Mobile Device Management (MDM)
For businesses providing mobile devices or supporting BYOD policies, MDM solutions streamline device configuration, app deployment, and security policy enforcement.
IT Service Management Platforms
These platforms coordinate the entire onboarding workflow, tracking progress across different teams and ensuring nothing falls through the cracks.
Working with experienced managed IT service providers can help you implement and optimize these systems without requiring extensive internal expertise.
Building Your Onboarding Transformation Plan
Start by mapping your current process from offer letter to full productivity. Identify bottlenecks, manual steps, and areas where new employees commonly experience friction.
Prioritize improvements based on impact and implementation difficulty. Often, simple changes like standardized checklists or automated reminders can dramatically improve the experience while you work toward more comprehensive automation.
Remember: excellent IT onboarding isn't just about technology: it's about demonstrating that your organization values efficiency, security, and employee experience from day one.
When new employees can log in seamlessly, access everything they need, and start contributing immediately, you've accomplished much more than smooth onboarding. You've shown them they've joined a company that has its operations figured out and invests in making their work life better.
That's the kind of first impression that leads to long-term employee satisfaction and business success.
Don't Let Outdated Tech Slow You Down: Build a Smart IT Refresh Plan

Monday morning, 9 AM: Your team lead's laptop freezes during the client presentation. Tuesday afternoon: The accounting computer crashes, losing two hours of work. Wednesday: The server hiccups, bringing email down for half the day.
If this sounds like your typical week, you're experiencing the hidden tax of outdated technology. Small businesses lose approximately 98 hours per year: equivalent to 12 full working days: due to technology issues like slow PCs, failing hardware, and outdated software.
That's nearly two and a half weeks of lost productivity per employee, every year. For a team of 10, you're looking at 25 weeks of wasted time annually. At an average cost of $50 per hour, that's $122,500 in lost productivity: far more than the cost of proactive technology refresh.
The math is clear: running outdated technology isn't saving money. It's bleeding money in ways you might not even notice.
Why Reactive IT Management Fails
The Emergency Replacement Trap
When computers fail unexpectedly, you're forced into emergency purchasing mode. You need a replacement immediately, which means paying premium prices for whatever's available quickly. Express shipping, rush setup, and crisis management all add unnecessary costs.
Emergency replacements also mean no time for proper research. You might end up with hardware that's incompatible with your existing systems or doesn't meet your actual requirements.
The Security Time Bomb
Older systems often can't run current security software or receive critical updates. Each month they remain in service, they become increasingly vulnerable to cyber threats. A single security breach can cost small businesses an average of $200,000: far exceeding any technology refresh budget.
The Productivity Death Spiral
As computers age, they slow down. Employees spend more time waiting for applications to load, files to save, and systems to respond. This gradual degradation is easy to ignore day-to-day, but the cumulative impact is massive.
When your team starts workarounds: restarting computers multiple times per day, avoiding certain applications because they're too slow, or manually doing tasks that should be automated: your productivity has already taken a serious hit.

Building a Strategic Refresh Plan
Asset Lifecycle Tracking
Start by creating a comprehensive inventory of all technology assets, including:
- Purchase dates and warranty information
- Current specifications and performance capabilities
- Software versions and support status
- Usage patterns and business criticality
This inventory becomes your refresh roadmap, helping you prioritize which systems need attention first and when replacements should be planned.
Establishing Refresh Cycles
Different types of technology have different optimal refresh cycles:
Laptops and Desktops: 3-4 years
Consumer-grade computers typically show significant performance degradation after three years. Business-grade machines can often stretch to four years, but performance improvements in newer generations usually justify replacement by year four.
Servers: 4-5 years
Server hardware is built for longevity, but performance gains and power efficiency improvements in newer generations provide compelling upgrade justifications every 4-5 years.
Network Equipment: 5-7 years
Routers, switches, and other network infrastructure can operate reliably for extended periods, but security updates and performance improvements may necessitate earlier replacement.
Mobile Devices: 2-3 years
Smartphones and tablets face rapid obsolescence due to operating system requirements and battery degradation.
Gradual Replacement Strategy
Instead of replacing everything at once, implement a rolling refresh schedule. Replace roughly 25-30% of your equipment each year, starting with the oldest and most critical systems.
This approach provides several benefits:
- Spreads costs across multiple budget cycles
- Maintains operational continuity during transitions
- Allows learning from early replacements to inform later decisions
- Reduces the risk of widespread system failures
Financial Planning for Technology Refresh
Budgeting Models
Annual Refresh Budget: Allocate a fixed percentage of revenue (typically 3-7% for small businesses) specifically for technology refresh. This creates predictable expenses and ensures funds are available when needed.
Depreciation-Based Planning: Set aside money each month based on the expected lifespan of each device. For a $1,200 laptop with a 3-year lifespan, budget $33 per month for its eventual replacement.
Financing and Leasing Options
Many businesses benefit from technology leasing programs that include automatic refresh cycles. These programs can provide:
- Predictable monthly expenses instead of large capital outlays
- Automatic upgrades at the end of lease terms
- Included support and warranty coverage
- Tax advantages in many jurisdictions
Cost-Saving Strategies
Business-Grade Equipment: While more expensive upfront, business-grade hardware typically lasts longer, includes better warranties, and offers superior support compared to consumer models.
Volume Purchasing: Coordinate refresh cycles to purchase multiple units simultaneously, leveraging volume discounts from vendors.
Trade-In Programs: Many manufacturers offer trade-in credits for older equipment, reducing the net cost of new purchases.
Refurbishment for Secondary Uses: Instead of discarding replaced equipment, consider refurbishing it for less critical applications or backup purposes.
Security Considerations in Refresh Planning
Operating System Support Lifecycles
Plan refresh cycles around operating system support schedules. When Microsoft or Apple stops providing security updates, systems become increasingly vulnerable regardless of their physical condition.
Compliance Requirements
Many industries have specific technology requirements for compliance. Healthcare organizations need HIPAA-compliant systems, financial services require specific security standards, and government contractors must meet various certification requirements.
Factor these compliance needs into refresh planning to avoid urgent replacements when audit requirements change.

Implementation Best Practices
Standardization Benefits
Maintain a limited number of standard configurations rather than allowing completely customized setups. Standardization provides:
- Easier support and troubleshooting
- Volume purchasing advantages
- Simplified backup and recovery procedures
- Faster deployment and setup processes
Migration Planning
Each refresh cycle should include detailed migration planning:
- Data backup and transfer procedures
- Software licensing and installation requirements
- User training for new features or interfaces
- Rollback plans in case of unexpected issues
Testing and Validation
Before deploying refreshed systems to production use:
- Test all critical applications and workflows
- Verify network connectivity and security settings
- Ensure backup and recovery procedures work correctly
- Train key users on any changes or new features
Working with IT Partners
Managing technology refresh cycles requires ongoing attention and expertise that many small businesses lack internally. Managed IT service providers can provide valuable support through:
Strategic Planning: Help develop multi-year refresh roadmaps aligned with business objectives and budget constraints.
Vendor Management: Leverage relationships with hardware vendors to secure better pricing and support terms.
Implementation Services: Handle migration, setup, and deployment activities to minimize business disruption.
Ongoing Monitoring: Track system performance and reliability to optimize refresh timing and identify issues before they become critical.
Measuring Success
Performance Metrics
Track key indicators of refresh program success:
- Average system age across your environment
- Help desk tickets related to hardware issues
- Employee productivity and satisfaction scores
- System downtime and reliability metrics
Financial Analysis
Calculate the return on investment from proactive refresh by measuring:
- Reduced emergency replacement costs
- Decreased IT support time and expenses
- Improved employee productivity and efficiency
- Avoided costs from security incidents or compliance violations
Your Next Steps
Start with a comprehensive audit of your current technology assets. Document everything: age, performance, business criticality, and replacement costs. This assessment will reveal immediate priorities and help you build a realistic refresh timeline.
Don't try to solve everything at once. Focus on the oldest, most critical systems first, then build momentum with a sustainable replacement schedule.
Remember: A smart IT refresh plan isn't just about buying new equipment. It's about building a technology foundation that supports your business growth instead of holding it back. When your team can work efficiently without technology friction, that's when you'll see the real return on your refresh investment.
The question isn't whether you can afford to refresh your technology. It's whether you can afford not to.
Save Time and Money by Automating Workflows with Power Automate

Every Monday morning, Sarah spends two hours copying data from emails into spreadsheets, routing approval requests to managers, and manually updating customer records across three different systems. She's talented, organized, and frustrated: because she knows there has to be a better way.
There is. In 2024, 85% of business leaders identified AI-powered automation as key to driving productivity and efficiency. The tools exist, they're accessible to small businesses, and they can eliminate exactly the kind of repetitive work that's eating up Sarah's time.
Microsoft Power Automate represents one of the most practical entry points into business process automation. It's designed for real people solving real problems, without requiring a computer science degree or massive IT budget.
What Is Power Automate?
Power Automate is Microsoft's workflow automation tool that creates "flows": automated sequences that handle repetitive tasks across different applications and services. Think of it as a digital assistant that can move data, trigger actions, and coordinate processes between the tools your business already uses.
The platform connects with hundreds of applications: from Microsoft 365 tools like Outlook and SharePoint to popular business systems like Salesforce, QuickBooks, and Slack. Once you create a flow, it runs automatically in the background, handling tasks that would otherwise require manual intervention.
Key capabilities include:
- Moving data between applications automatically
- Triggering actions based on specific events or schedules
- Routing approvals and notifications
- Processing and organizing documents
- Synchronizing information across multiple systems
Why Small Businesses Should Care
Time Recovery
The average knowledge worker spends 2.5 hours per day on repetitive, administrative tasks. For a team of 10 employees, that's 25 hours daily spent on work that could be automated. Even if automation only recovers half that time, you're looking at 62.5 hours per week that can be redirected toward revenue-generating activities.
Consistency and Accuracy
Manual processes are prone to errors, especially when people are tired, rushed, or distracted. Automated workflows execute the same steps exactly the same way every time. They don't forget steps, make transcription errors, or skip validation checks.
Scalability Without Proportional Costs
As your business grows, manual processes become increasingly expensive and time-consuming. Automated workflows can handle 10 transactions or 10,000 transactions with the same efficiency. The marginal cost of additional volume is essentially zero.
Improved Customer Experience
Automation can dramatically improve response times and service consistency. When customer inquiries trigger automatic workflows that create support tickets, notify the right team members, and send acknowledgment emails, customers receive faster, more professional service.
Practical Automation Examples
Email and Document Management
One of the most immediate applications involves handling email attachments and document routing:
Automatic File Organization: When emails arrive with specific types of attachments (invoices, contracts, resumes), Power Automate can automatically save them to designated SharePoint folders or OneDrive locations with standardized naming conventions.
Document Approval Workflows: Instead of manually routing contracts or proposals through approval chains, create flows that automatically send documents to the right approvers based on amount thresholds, department requirements, or other business rules.
Email Response Management: Set up automatic acknowledgment emails for common inquiry types, ensuring customers receive immediate confirmation that their requests have been received and are being processed.
[IMAGE_HERE]
Employee Onboarding and HR Processes
New Hire Workflows: When HR enters a new employee into your system, Power Automate can trigger multiple parallel processes: creating accounts in various systems, assigning equipment, scheduling orientation sessions, and notifying relevant team members.
Time-Off Request Processing: Automate vacation request approvals by routing requests to the appropriate managers, checking available leave balances, and updating calendars once approved.
Performance Review Coordination: Automatically schedule performance review meetings, send reminder notifications, and collect feedback forms from multiple stakeholders.
Sales and Customer Relationship Management
Lead Processing: When new leads arrive from your website, trade shows, or other sources, automatically create records in your CRM, assign them to appropriate sales representatives, and trigger follow-up email sequences.
Customer Onboarding: Once a deal closes, automatically initiate customer onboarding workflows that create project folders, schedule kickoff meetings, and send welcome packages with relevant documentation.
Follow-Up Automation: Set up flows that automatically schedule follow-up tasks based on customer interactions, ensuring no leads fall through the cracks and all customers receive consistent attention.
Financial and Administrative Tasks
Invoice Processing: Automatically route invoices to appropriate approvers based on vendor, amount, or department, then update accounting systems once approved.
Expense Report Management: Create workflows that validate expense submissions, route them for approval, and integrate approved expenses with your accounting platform.
Inventory and Ordering: Monitor inventory levels automatically and trigger purchase orders or alerts when stock falls below predetermined thresholds.
Getting Started: A Practical Approach
Identify High-Impact Opportunities
Start by documenting repetitive tasks your team performs regularly. Look for processes that involve:
- Moving data between systems
- Routing items for approval or review
- Sending notifications or status updates
- Creating records or reports based on standardized information
Start Simple
Your first automation should be straightforward and low-risk. Good beginner projects include:
- Saving email attachments to cloud storage
- Creating calendar events from form submissions
- Sending automatic acknowledgment emails
- Copying data between spreadsheets and databases
Test Thoroughly
Before deploying any automation to production, test it extensively with sample data. Verify that it handles edge cases appropriately and includes proper error handling. Start with small-scale implementations before expanding to larger processes.
[IMAGE_HERE]
Building Effective Workflows
Design for Reliability
Error Handling: Include steps that handle exceptions gracefully. If an automated email fails to send, the workflow should log the error, notify administrators, and potentially try alternative delivery methods.
Monitoring and Logging: Configure flows to track their execution and performance. You need visibility into what's working, what's failing, and where bottlenecks occur.
Security and Permissions
Access Controls: Ensure automated workflows only access data and systems they actually need. Follow principle of least privilege when configuring system connections.
Approval Gates: For workflows involving financial transactions or sensitive data, include human approval steps at critical decision points.
Data Privacy: Consider how automated workflows handle sensitive information and ensure they comply with relevant privacy regulations.
Integration Strategies
Microsoft 365 Ecosystem
Power Automate integrates seamlessly with other Microsoft tools:
- Outlook: Process emails, calendar events, and contacts
- SharePoint: Manage documents, lists, and collaboration workflows
- Teams: Send notifications and coordinate team activities
- Excel: Update spreadsheets and create reports automatically
Third-Party Applications
The platform includes connectors for hundreds of popular business applications:
- CRM Systems: Salesforce, HubSpot, Dynamics 365
- Accounting Software: QuickBooks, Xero, FreshBooks
- Communication Tools: Slack, Zoom, Twilio
- E-commerce Platforms: Shopify, WooCommerce, Magento
Custom Integrations
For specialized applications or unique requirements, Power Automate supports custom connectors and API integrations, allowing you to automate processes involving virtually any system that provides programmatic access.
Measuring Success
Quantifiable Benefits
Track specific metrics to measure automation impact:
- Time saved per process execution
- Reduction in manual errors and rework
- Faster processing times for customer requests
- Decreased administrative overhead
Employee Satisfaction
Survey team members about their experience with automated processes:
- Are they spending more time on high-value activities?
- Has their job satisfaction improved with less repetitive work?
- What additional processes would they like to see automated?
Business Impact
Connect automation initiatives to broader business objectives:
- Improved customer satisfaction scores
- Faster sales cycle times
- Reduced operational costs
- Enhanced compliance and audit readiness
Implementation Support
While Power Automate is designed to be user-friendly, successful automation often benefits from expert guidance. Managed IT service providers can help with:
Strategic Planning: Identify the highest-impact automation opportunities for your specific business
Technical Implementation: Design and build reliable, scalable workflows
Training and Support: Ensure your team can maintain and expand automation capabilities
Integration Expertise: Connect Power Automate with your existing business systems effectively
Your Automation Journey
Start with a simple process that your team finds annoying or time-consuming. Success with initial automations builds confidence and expertise for tackling more complex workflows later.
Remember: automation isn't about replacing human judgment: it's about eliminating human drudgery. When your team isn't bogged down with repetitive tasks, they can focus on strategy, creativity, and relationships that actually drive business growth.
The question isn't whether your business can benefit from automation. It's which processes you'll automate first to start reclaiming time and improving efficiency immediately.
Securing Your Supply Chain: Practical Cybersecurity Steps for Small Businesses

Your company's cybersecurity is only as strong as its weakest link. And increasingly, that weak link isn't inside your organization: it's somewhere in your supply chain.
Picture this scenario: Your business has excellent firewalls, employee training, and security protocols. But a software vendor you rely on gets breached, and suddenly cybercriminals have access to your systems through that trusted connection. Or a cloud service provider experiences a data leak that exposes your customer information stored on their servers.
This isn't theoretical. 60% of small business breaches now originate in the supply chain rather than through direct attacks. Cybercriminals have learned it's often easier to compromise a trusted vendor and use that relationship to access multiple targets than to attack each business individually.
For small businesses, supply chain security can feel overwhelming. You're already managing relationships with dozens of vendors, contractors, and service providers. How can you possibly evaluate and monitor the security practices of every company you work with?
The answer lies in systematic, practical approaches that protect your business without requiring a dedicated cybersecurity team.
Understanding Your Supply Chain Risk
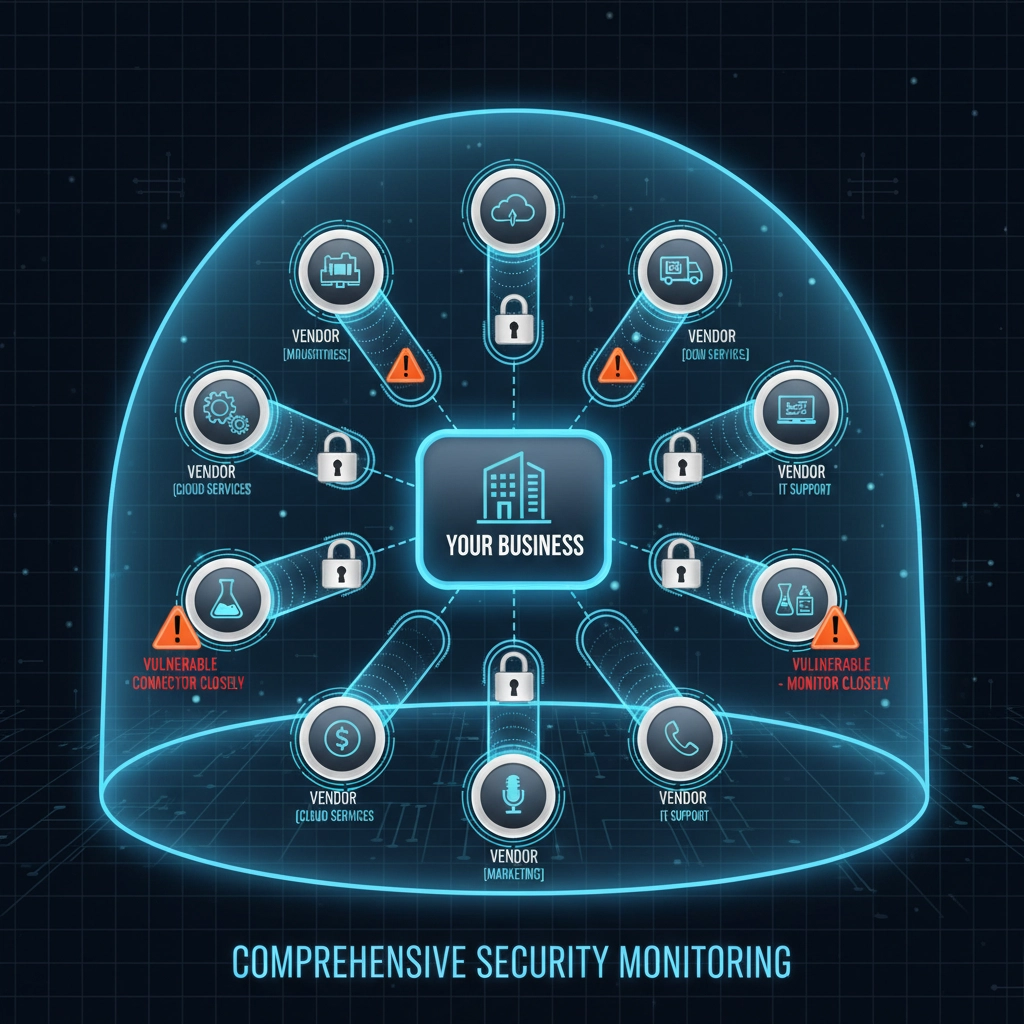
Mapping Your Vendor Ecosystem
Start by creating a comprehensive inventory of every organization that has access to your systems, data, or facilities. This includes:
Technology Vendors
- Software providers (CRM, accounting, email systems)
- Cloud service providers (hosting, backup, collaboration tools)
- IT support companies and consultants
- Hardware suppliers and maintenance providers
Service Providers
- Legal and accounting firms
- Marketing agencies and consultants
- Cleaning and maintenance companies
- Shipping and logistics partners
Financial Partners
- Banks and payment processors
- Insurance providers
- Investment and retirement plan administrators
Many businesses discover they have relationships with far more vendors than initially realized. Each represents a potential entry point for cybercriminals.
[IMAGE_HERE]
Risk Assessment and Prioritization
Not all vendor relationships carry equal risk. Prioritize your security efforts by evaluating:
Data Access Level: Which vendors can access sensitive customer information, financial records, or proprietary business data?
System Integration Depth: Which vendors have administrative access to your networks, applications, or infrastructure?
Business Criticality: Which vendors provide services essential to daily operations? A breach affecting these relationships could shut down your business.
Vendor Security History: Which vendors have experienced previous security incidents or have questionable security practices?
Focus your most intensive security requirements on high-risk relationships while applying baseline standards to all vendors.
Due Diligence and Vendor Assessment
Security Questionnaires and Assessments
Develop standardized security questionnaires for different vendor types. Key areas to evaluate include:
Data Protection Practices
- How is sensitive data encrypted in transit and at rest?
- What access controls and authentication methods are used?
- Where is data stored geographically, and under what legal jurisdiction?
- What are their data retention and disposal practices?
Incident Response Capabilities
- What is their process for detecting and responding to security incidents?
- How quickly do they notify customers of potential breaches?
- What support do they provide during and after security incidents?
Compliance and Certifications
- Do they maintain relevant security certifications (SOC 2, ISO 27001, etc.)?
- How do they ensure compliance with industry regulations?
- Can they provide recent audit reports or security assessments?
Business Continuity Planning
- What backup systems and disaster recovery plans do they have?
- How do they ensure service availability during emergencies?
- What are their uptime guarantees and compensation policies?
[IMAGE_HERE]
Contractual Security Requirements
Incorporating Security Clauses
Your contracts should include specific security requirements and expectations:
Data Protection Requirements
- Minimum encryption standards for data handling
- Restrictions on data sharing with third parties
- Requirements for secure data deletion when relationships end
- Compliance with relevant privacy regulations (GDPR, CCPA, HIPAA)
Incident Notification Obligations
- Timeline requirements for breach notifications (typically 24-72 hours)
- Types of incidents that must be reported
- Information that must be included in notifications
- Contact procedures for emergency situations
Audit and Monitoring Rights
- Your right to review security practices and audit results
- Requirements for regular security assessments
- Access to compliance reports and certifications
- Procedures for addressing identified security deficiencies
Liability and Insurance Requirements
- Minimum cybersecurity insurance coverage levels
- Liability allocation for security incidents and data breaches
- Indemnification clauses protecting your business
- Requirements for maintaining insurance throughout the relationship
Ongoing Monitoring and Management
Regular Security Reviews
Vendor security isn't a one-time assessment. Establish regular review cycles:
Annual Comprehensive Reviews: Detailed security assessments for high-risk vendors, including updated questionnaires, audit reports, and compliance certifications.
Quarterly Check-ins: Brief status updates on security practices and any significant changes in their operations or risk profile.
Incident-Triggered Reviews: Immediate assessments following any security incident affecting the vendor or their industry.
News and Intelligence Monitoring: Regular review of security news and threat intelligence related to your vendors and their technologies.
Performance Monitoring
Track key security indicators for critical vendors:
- Response times for security-related requests
- Frequency and severity of security incidents
- Compliance with contractual security requirements
- Quality of security communications and reporting
[IMAGE_HERE]
Zero Trust Principles
Never Trust, Always Verify
Traditional security assumed that trusted vendors could be given broad access to your systems. Zero trust assumes that every access request: even from trusted partners: must be verified and limited.
Practical Zero Trust Implementation:
Least Privilege Access: Vendors receive only the minimum access necessary to perform their specific functions. No blanket administrative access.
Multi-Factor Authentication: All vendor access to your systems requires strong authentication, regardless of the vendor's internal security practices.
Network Segmentation: Vendor access is isolated from your core business systems and sensitive data whenever possible.
Continuous Monitoring: All vendor activities on your systems are logged and monitored for unusual behavior or policy violations.
Session Management: Vendor access sessions have defined time limits and must be renewed regularly rather than remaining permanently active.
Incident Response and Recovery
Breach Response Planning
Develop specific procedures for supply chain security incidents:
Immediate Response Actions
- Isolation procedures to prevent further compromise
- Communication protocols for notifying affected stakeholders
- Evidence preservation requirements for potential legal proceedings
- Alternative vendor arrangements to maintain business operations
Investigation and Assessment
- Procedures for determining the scope and impact of vendor breaches
- Coordination with law enforcement and regulatory authorities
- Communication strategies for customers, employees, and other stakeholders
- Documentation requirements for insurance claims and legal proceedings
Recovery and Lessons Learned
- Criteria for restoring vendor relationships after security incidents
- Process improvements based on incident analysis
- Updates to security requirements and assessment procedures
- Enhanced monitoring and controls for affected vendor relationships
Building Security Culture
Employee Training and Awareness
Your team needs to understand supply chain security risks and their role in managing them:
Vendor Management Training: Education on security assessment procedures, contract review requirements, and escalation processes for security concerns.
Social Engineering Awareness: Training to recognize vendor impersonation attempts and fraudulent communications claiming to be from trusted partners.
Incident Reporting Procedures: Clear instructions for reporting suspected vendor security issues or unusual activities.
Regular Updates: Ongoing communication about emerging supply chain threats and updated security procedures.
Technology Solutions
Vendor Risk Management Platforms
Specialized tools can help automate and scale supply chain security management:
- Automated security questionnaire distribution and collection
- Continuous monitoring of vendor security ratings and threat intelligence
- Integration with contract management and procurement systems
- Dashboard reporting on vendor risk profiles and compliance status
Security Information Sharing
Participate in industry security information sharing programs to stay informed about:
- Emerging threats targeting your industry or vendor ecosystem
- Security incidents affecting commonly used vendors or technologies
- Best practices and lessons learned from other organizations
- Regulatory updates and compliance requirements
[IMAGE_HERE]
Working with Security Experts
Managing supply chain security effectively often requires expertise that small businesses lack internally. Managed IT service providers can provide valuable support through:
Vendor Assessment Services: Professional evaluation of vendor security practices and risk profiles
Contract Review Support: Assistance incorporating appropriate security clauses and requirements
Monitoring and Intelligence: Ongoing surveillance of vendor security status and threat landscape
Incident Response Support: Expert assistance during supply chain security incidents
Your Next Steps
Start with a comprehensive inventory of your current vendor relationships and their access to your systems and data. This baseline assessment will help you prioritize security efforts and identify immediate concerns.
Focus on your highest-risk relationships first: vendors with access to sensitive data or critical business systems. Implement baseline security requirements for all vendors, but invest your time and resources in thoroughly securing the relationships that could cause the most damage if compromised.
Remember: supply chain security isn't about eliminating all risk: it's about understanding, managing, and monitoring risk appropriately. The goal is building a vendor ecosystem that supports your business growth while maintaining security standards that protect your customers, employees, and competitive advantages.
When supply chain security becomes a systematic part of your vendor management process, you transform potential vulnerabilities into competitive advantages through superior risk management and operational resilience.
Building a Smart Data Retention Policy: What Your Small Business Needs to Keep (and Delete)
Maria opened her company's file server and stared at 15 years' worth of digital documents. Employee records from people who left a decade ago. Contracts for projects completed in 2010. Thousands of emails that might or might not be important. Customer data from clients she wasn't sure were still active.
She needed to find last month's financial reports for the accountant, but they were buried somewhere in this digital hoarding pile. Every search took forever. Storage costs were climbing. And she had an unsettling feeling that keeping all this old information might actually be creating legal and security risks rather than protecting her business.
Sound familiar? A study by PR Newswire found that 72% of business leaders have delayed important decisions because data was too overwhelming. Your information should enable better decision-making, not paralyze it.
The solution isn't keeping everything forever "just in case." It's building a smart data retention policy that keeps what you need, discards what you don't, and organizes everything so you can actually find it when necessary.
Why Data Retention Policies Matter
Legal and Compliance Requirements
Different types of business information have specific retention requirements under various laws and regulations:
Financial Records: The IRS generally requires businesses to keep tax-related documents for at least three years, with some exceptions extending to seven years. State requirements may vary.
Employment Records: Federal law requires maintaining personnel files for specific periods after employment ends: typically 1-7 years depending on the type of record and company size.
Customer Data: Privacy regulations like GDPR and CCPA not only govern how you collect and use customer data but also require deleting it when no longer needed for legitimate business purposes.
Industry-Specific Requirements: Healthcare, financial services, government contractors, and other regulated industries have additional retention requirements that can extend decades.
Keeping records too briefly can result in compliance violations. Keeping them too long can create unnecessary legal exposure and privacy risks.
Cost and Efficiency Considerations
Data storage isn't free, and the costs compound over time:
Storage Costs: Cloud storage, server space, and backup systems all charge based on the volume of data you maintain. Unnecessary historical data can represent significant ongoing expenses.
Performance Impact: Overstuffed systems slow down searches, backups, and routine operations. When employees can't find information quickly, productivity suffers.
Security Risks: Every piece of stored data represents a potential security liability. Old customer information, defunct employee records, and obsolete business documents can all be compromised in a breach, creating legal exposure long after their business value has expired.
[IMAGE_HERE]
Core Components of a Data Retention Policy
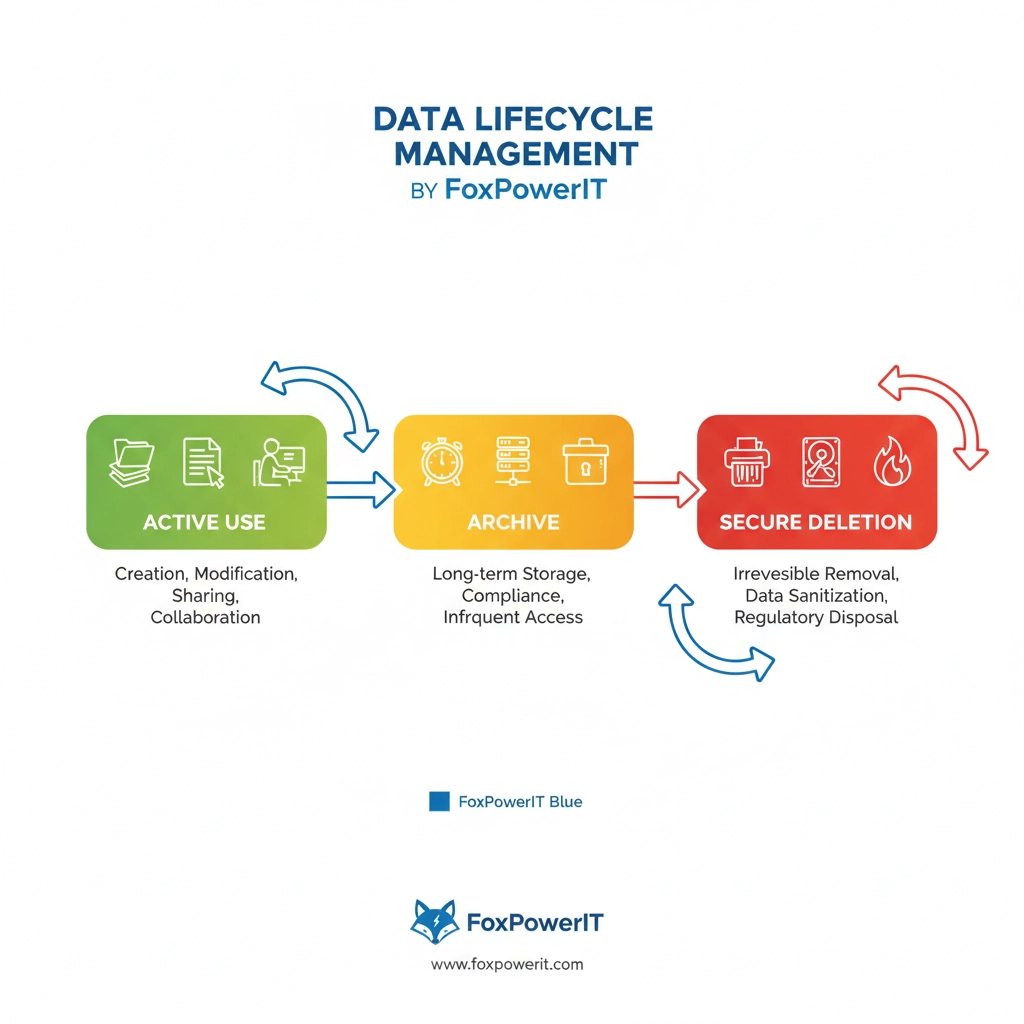
Data Classification System
Not all business information has the same value, legal requirements, or security implications. Develop clear categories:
Critical Business Records
- Financial statements and tax documents
- Legal contracts and agreements
- Intellectual property and trade secrets
- Regulatory compliance documentation
- Insurance policies and claims
Operational Data
- Customer relationship information
- Employee personnel files
- Vendor and supplier records
- Project documentation and communications
- Marketing and sales materials
Temporary Information
- Draft documents and working files
- Routine email communications
- Meeting notes and informal communications
- Temporary project files
- System logs and backup files
Each category should have specific retention periods, storage requirements, and disposal procedures.
Retention Schedules by Data Type
Financial and Accounting Records
- Tax returns and supporting documents: 7 years
- General financial statements: 7 years
- Accounts payable/receivable: 7 years
- Bank statements and reconciliations: 7 years
- Payroll records: 4 years after termination
Human Resources Documentation
- Personnel files: 7 years after termination
- I-9 forms: 3 years after hire or 1 year after termination (whichever is later)
- Benefits enrollment and claims: 6 years
- Safety training records: 5 years
- Performance reviews: 3 years after termination
Customer and Sales Information
- Customer contracts: 7 years after completion
- Sales records and invoices: 7 years
- Customer communications: 3 years unless part of ongoing relationship
- Marketing campaign data: 3 years
- Website analytics: 2 years
Operational Records
- Vendor contracts: 7 years after expiration
- Insurance policies: Permanent (active) / 7 years (expired)
- Meeting minutes (board/management): Permanent
- Routine meeting notes: 1 year
- Project documentation: 5 years after completion
[IMAGE_HERE]
Implementation Strategies
Automated Classification and Retention
Manual data management is time-intensive and error-prone. Modern systems can automate much of the process:
Email Management: Configure email systems to automatically archive or delete messages based on age, sender, or content classification. Set up separate retention rules for different types of business communications.
Document Management Systems: Implement systems that automatically classify documents based on content, source, or metadata, then apply appropriate retention schedules.
Database Maintenance: Set up automated processes to archive or purge old records from customer databases, employee systems, and operational applications.
Cloud Storage Policies: Most cloud platforms include lifecycle management features that can automatically move older data to cheaper storage tiers or delete it entirely based on your retention schedules.
Archive Systems
Not all data needs immediate access, but some information must be retained for legal or business purposes:
Tiered Storage: Move older, rarely-accessed data to cheaper storage options while keeping recent information readily available.
Search and Retrieval: Ensure archived data remains searchable and retrievable when needed for legal, audit, or business purposes.
Format Preservation: Plan for technology changes that might make archived data inaccessible in the future. Consider migration strategies for critical long-term records.
Privacy and Security Considerations
Data Minimization Principles
Modern privacy regulations emphasize collecting and retaining only the data necessary for legitimate business purposes:
Purpose Limitation: Keep personal data only as long as needed for the specific purpose for which it was collected.
Regular Review: Periodically assess whether you still have legitimate business needs for personal data in your systems.
Consent Management: If you collected data based on customer consent, retention periods should align with the scope of that consent.
Individual Rights: Customers may have rights to request deletion of their personal data, which your retention policy must accommodate.
Secure Disposal Procedures
Simply deleting files doesn't guarantee they're truly gone. Implement secure disposal practices:
Data Destruction Standards: Use secure deletion methods that overwrite data multiple times, making it unrecoverable.
Certificate of Destruction: For sensitive information, obtain certificates confirming that data has been securely destroyed according to recognized standards.
Third-Party Data: Ensure vendors and service providers follow equally rigorous disposal procedures for data they handle on your behalf.
Physical Media: Develop procedures for securely destroying hard drives, backup tapes, and other physical storage media.
[IMAGE_HERE]
Legal Hold and Exception Management
Litigation and Investigation Holds
Sometimes legal requirements override normal retention schedules:
Legal Hold Procedures: When litigation is anticipated or investigations begin, implement holds that preserve all relevant data regardless of normal retention periods.
Scope Definition: Clearly define what data must be preserved, who is responsible for implementation, and how to communicate holds to relevant team members.
Duration Management: Regularly review active legal holds and release them when no longer required, allowing normal retention schedules to resume.
Documentation: Maintain detailed records of all legal holds, including implementation dates, scope, and release authorization.
Exception Handling
Your retention policy should include procedures for managing exceptions:
Business Justification: Require clear business reasons for retaining data beyond standard schedules.
Approval Processes: Define who can authorize retention exceptions and what documentation is required.
Review Cycles: Regularly review exceptions to ensure they remain necessary and appropriate.
Risk Assessment: Evaluate the legal, security, and cost implications of retention exceptions.
Training and Compliance
Employee Education
Your retention policy only works if employees understand and follow it:
Role-Specific Training: Different employees need different levels of detail about retention requirements and procedures.
Regular Updates: Conduct annual training updates and communicate policy changes promptly.
Practical Guidance: Provide clear examples and decision trees to help employees apply retention policies in daily work.
Responsibility Assignment: Clearly define who is responsible for retention decisions in different business areas.
Monitoring and Auditing
Compliance Checks: Regularly audit data retention practices to ensure policies are being followed consistently.
System Reviews: Verify that automated retention systems are working correctly and haven't been bypassed or misconfigured.
Policy Effectiveness: Assess whether retention periods are appropriate based on actual business needs and legal requirements.
Corrective Actions: Develop procedures for addressing policy violations or system failures.
Technology Tools and Support
Effective data retention often requires specialized tools and expertise. Managed IT service providers can help implement and maintain retention systems through:
Policy Development: Professional assistance creating retention schedules tailored to your industry and business model
System Implementation: Configuration of automated retention and archiving systems
Compliance Monitoring: Ongoing oversight to ensure retention practices meet legal and regulatory requirements
Secure Disposal: Professional data destruction services with proper certification and documentation
Measuring Success
Key Performance Indicators
Track metrics that demonstrate your retention policy's effectiveness:
- Percentage reduction in storage costs after implementation
- Time savings in data searches and retrieval
- Compliance audit results and violation reduction
- Employee satisfaction with data accessibility and organization
Return on Investment
Calculate the value of effective data retention:
- Reduced storage and backup costs
- Decreased legal and compliance risks
- Improved employee productivity through better data organization
- Enhanced security posture through reduced data exposure
Your Implementation Plan
Start by conducting a comprehensive audit of your current data landscape. Document what you have, where it's stored, and why you're keeping it. This baseline assessment will reveal immediate opportunities for cleanup and help you prioritize retention policy development.
Focus on high-risk data first: customer information, financial records, and employee data that have clear legal requirements. Implement automated retention for these categories before expanding to less critical information.
Remember: a good data retention policy is a balance between keeping what you need and eliminating what you don't. When you get this balance right, your data becomes a strategic asset that supports decision-making rather than a liability that drains resources and creates risks.
The goal isn't perfect data management: it's practical data management that serves your business objectives while meeting legal obligations and maintaining appropriate security standards.

