You walk into your dental practice Monday morning, grab your coffee, and check your emails. Buried between appointment confirmations and supply orders sits a message that makes your stomach drop: "Notice of Investigation from the Office for Civil Rights."
Your first thought? "We're careful with patient information."
Your second thought? "How much is this going to cost?"
If you're running a dental practice in Connecticut, that second thought should terrify you more than the first.
The $50,000 Reality Check
Connecticut dental practices are getting slammed with HIPAA violations that average $50,000 per incident: and some practices are paying as much as $70,000 for serious infractions. This isn't happening to careless practices that ignore privacy rules. It's happening to well-meaning dentists who think they're doing everything right.
Here's what most practice owners don't realize: over 90% of dental offices qualify as HIPAA covered entities because they electronically transmit health information for insurance claims and treatment authorizations. The moment you submit a digital claim, you're playing by the same rules as massive hospital systems.
And the Department of Health and Human Services isn't interested in your practice size when they calculate fines.

Why Good Practices Are Getting Caught
The violations aren't happening because dentists don't care about patient privacy. They're happening because of operational oversights that seem minor until an investigator shows up.
Take Gums Dental, a solo practice that got hit with a $70,000 fine. Their violation? Failing to provide patient access to medical records despite repeated requests over two years. No data breach. No malicious intent. Just a broken process that cost them the equivalent of a luxury car.
Willful neglect violations carry penalties ranging from $68,928 to $2,067,813 per incident. And "willful neglect" doesn't mean you intentionally violated HIPAA: it means you knew about a problem and didn't fix it fast enough.
The most common violations include:
- Improper disposal of appointment schedules and treatment notes
- Unsecured communications about patient cases
- Inadequate access controls with shared login credentials
- Mobile device security breaches from unprotected tablets
These aren't theoretical risks. They're the exact violations that have cost Connecticut practices hundreds of thousands of dollars in the past year alone.
The 5-Step IT Security Checklist That Prevents HIPAA Fines
Most dental practices think HIPAA compliance is about training staff not to gossip about patients. That's part of it, but the real money is lost on IT security failures. Here's your defense system:
Step 1: Lock Down Your Access Controls
Every person in your practice needs their own unique login credentials. No shared passwords. No "temporary" access that becomes permanent.
Set up automatic logouts after 15 minutes of inactivity. If someone steps away from their workstation, the system locks itself. Configure role-based access so your hygienist can't accidentally access financial records they don't need.
Conduct quarterly access reviews. When someone leaves your practice, their access gets terminated that day: not next week when you remember to call your IT guy.
Step 2: Secure Every Communication Channel
Patient information can't travel through regular email, text messages, or voicemail systems. Period.
Install encrypted email systems for any patient-related communications. Use secure messaging platforms for internal staff discussions about cases. Train your team that patient conversations happen in private spaces: never at the front desk where other patients can hear.
Set up encrypted voicemail with automatic deletion schedules so sensitive messages don't sit in your system indefinitely.

Step 3: Build Mobile Device Security Protocols
Your tablets and smartphones are security vulnerabilities waiting to happen. Every device that accesses patient information needs password protection and automatic locking.
Install encryption software on tablets used for patient check-ins or treatment planning. Create a device inventory system that tracks security updates and ensures every device stays current.
Most importantly, develop remote wipe capabilities. If a device gets lost or stolen, you can erase all patient data before someone accesses it.
Step 4: Create Bulletproof Data Disposal Procedures
Those appointment schedules you throw in the regular trash? Those printed treatment notes in your recycling bin? Each one is a potential $50,000 violation.
Install industrial-grade shredders for all printed patient materials. Establish digital data wiping protocols that permanently erase information from hard drives and storage devices.
Schedule regular disposal audits to ensure your staff follows procedures consistently. Train everyone on proper disposal techniques for different types of patient information.
Step 5: Implement Regular Security Training and Monitoring
Here's a sobering statistic: only 70% of dental practices conduct regular HIPAA training. If you're in the 30% that doesn't, you're practically inviting a violation.
Provide annual HIPAA training sessions for all staff members. Perform monthly security risk assessments of your IT systems. Document every training session and security incident: investigators want to see your paper trail.
Establish clear incident response procedures. When something goes wrong, your team needs to know exactly what to do and who to call.

The Simple Truth About HIPAA Compliance
HIPAA violations aren't random bad luck: they're predictable system failures. Practices that get fined usually have gaps in their processes, not gaps in their intentions.
The difference between a $50,000 fine and sleeping peacefully at night comes down to having systems that work even when people make mistakes. Your compliance isn't about being perfect. It's about being prepared.
The stakes have never been higher for Connecticut dental practices in 2025. Reputation damage from HIPAA violations often costs more than the actual fines, leading to patient attrition and difficulty attracting new patients.
But here's the good news: every violation on this checklist is preventable with the right systems and training.
Start with Step 1 this week. Pick one access control issue in your practice and fix it. Then move to Step 2 next week. Small, consistent improvements will build a compliance system that protects both your patients and your practice.
Your patients trust you with their health. Make sure your IT systems are worthy of that trust.
Need help implementing these HIPAA security measures? FoxPowerIT specializes in compliance assistance for Connecticut healthcare practices. Get your free security assessment today.
Connecticut's New Privacy Law Hits July 2026: Are You Making These 7 Critical Data Protection Mistakes?

Your customer database contains 15,000 Connecticut residents. Your website tracks visitor behavior. Your email system stores years of communications with clients.
On July 1, 2026, Connecticut's comprehensive data privacy law goes into effect: and suddenly, every piece of personal information your business handles becomes a potential compliance landmine.
Most Connecticut SMBs are making the same mistake: assuming they have time to figure this out later. But "later" is 18 months away, and the businesses that wait until 2026 to start preparing will spend their July 4th weekend dealing with panic-mode compliance instead of barbecues.
Why This Law Changes Everything
Connecticut's Act Concerning Personal Data Privacy and Online Monitoring (CTDPA) isn't just another regulation you can ignore. It applies to any business that processes personal data of 100,000+ Connecticut residents annually or derives revenue from selling personal data of 25,000+ Connecticut residents.
If those numbers sound high, think again. A local restaurant chain with online ordering, a dental practice with digital patient records, or a retail shop with email marketing can easily hit these thresholds.
The law grants Connecticut residents five fundamental rights:
- Right to access their personal data
- Right to delete their personal data
- Right to correct inaccurate information
- Right to data portability
- Right to opt out of data sales and targeted advertising
Each violation can result in fines up to $5,000 per incident. With automatic enforcement starting day one, there's no grace period for businesses that aren't ready.
The 7 Critical Mistakes Connecticut SMBs Are Making
Mistake #1: Assuming You Don't Collect "Personal Data"
Personal data isn't just names and social security numbers. Under CTDPA, it includes IP addresses, device identifiers, geolocation data, and biometric information. Your website analytics, security cameras, and even your Wi-Fi logs might contain regulated personal data.
Mistake #2: Ignoring Your Website's Data Collection
Your website's contact forms, cookies, and tracking pixels are data collection points that need CTDPA compliance. Many SMBs don't realize their Google Analytics setup or Facebook pixel is collecting personal data that triggers reporting requirements.
Mistake #3: No Data Inventory System
You can't comply with data deletion requests if you don't know where customer data lives in your systems. Most businesses store personal data in CRM systems, email platforms, payment processors, cloud storage, and backup systems: but have no centralized inventory.
Mistake #4: Relying on Generic Privacy Policies
Those template privacy policies downloaded from legal websites won't cut it. CTDPA requires specific language about data collection, processing purposes, retention periods, and consumer rights. Generic policies leave you exposed to violations.
Mistake #5: No Consumer Request Response System
When Connecticut residents request access to their data or demand deletion, you have 45 days to respond (with possible 45-day extension). Without systems to track, process, and document these requests, you'll miss deadlines and face penalties.
Mistake #6: Inadequate Vendor Agreements
Your payment processor, email service, and cloud storage providers all handle customer data on your behalf. Under CTDPA, you're responsible for ensuring these vendors protect Connecticut resident data appropriately through proper contractual agreements.
Mistake #7: No Employee Training Program
Data privacy isn't just an IT issue: it's a company-wide responsibility. Employees who handle customer data need training on CTDPA requirements, data handling procedures, and incident response protocols.

Your 18-Month Compliance Roadmap
Months 1-3: Discovery and Assessment
- Conduct comprehensive data inventory across all systems
- Map data flows from collection through disposal
- Identify which processes trigger CTDPA requirements
- Assess current privacy policy and procedures
Months 4-6: System Implementation
- Deploy consumer request management system
- Update privacy policies with CTDPA-compliant language
- Implement data retention and deletion procedures
- Negotiate vendor agreements with privacy protections
Months 7-12: Process Development
- Create employee training materials and schedules
- Establish incident response procedures
- Develop data breach notification protocols
- Test consumer request response workflows
Months 13-18: Final Preparation
- Conduct compliance audits and testing
- Train all staff on new procedures
- Update website privacy notices and consent mechanisms
- Prepare for July 1, 2026 enforcement
The Competitive Advantage Hidden in Compliance
Here's what most businesses miss: CTDPA compliance isn't just about avoiding fines: it's about building customer trust that drives revenue.
Connecticut consumers are increasingly privacy-conscious. Businesses that proactively implement strong data protection practices and communicate them clearly will differentiate themselves from competitors scrambling to comply.
The companies that view CTDPA as an opportunity to improve their data practices will emerge stronger. The ones that treat it as a burden to minimize will struggle with both compliance and customer confidence.
Start your CTDPA compliance planning now, not next year. The businesses that begin preparing today will have 18 months to implement robust systems. The ones that wait will have 18 weeks to panic.
Your customer data is an asset worth protecting: make sure your protection systems are worthy of your customers' trust.
Need help navigating Connecticut's new privacy law? FoxPowerIT provides compliance assistance specifically designed for Connecticut SMBs. Schedule your CTDPA readiness assessment today.
Vulnerability Scanning vs. Network Monitoring: Which Protects Your Connecticut Business Better Against the 300% Rise in SMB Ransomware?

You're running a successful Connecticut manufacturing company with 47 employees. Last Tuesday, your operations manager couldn't access the inventory system. Wednesday, your accounting software started running slowly. Thursday morning, every screen in your office displayed the same message: "Your files have been encrypted. Pay $75,000 in Bitcoin within 72 hours or lose everything."
Welcome to the new reality of SMB ransomware.
Ransomware attacks on small and medium businesses have increased 300% since 2022, and Connecticut companies are getting hit harder than the national average. But here's what most business owners don't understand: the cybersecurity tools meant to protect you aren't created equal.
You've probably heard about vulnerability scanning and network monitoring. You might even think they're the same thing. They're not: and choosing the wrong one could be the difference between staying in business and shutting down after an attack.
The Tale of Two Security Approaches
Vulnerability scanning is like getting a comprehensive health checkup for your IT systems. It examines your network, identifies weaknesses, and produces a report showing every potential entry point attackers might exploit.
Network monitoring is like having a 24/7 security guard watching your digital premises. It continuously observes network traffic, user behavior, and system activities to detect threats in real-time.
Both sound important. Both are sold as "essential cybersecurity." But only one will save your business when ransomware strikes at 2 AM on a Saturday.
Why Vulnerability Scanning Fails When It Matters Most
Vulnerability scanning is reactive by nature. It shows you problems that exist but does nothing to stop active attacks.
Consider a real Connecticut case study: A local accounting firm ran quarterly vulnerability scans that consistently showed their systems were "low risk." Their firewall was updated, their software was patched, and their report showed green checkmarks across the board.
But vulnerability scans can't detect social engineering attacks. When an employee clicked a malicious email link during tax season, ransomware spread through their network in 37 minutes. The vulnerability scan hadn't identified the real weakness: human behavior and lateral network movement.
Vulnerability scanning has three critical limitations:
Point-in-Time Analysis: Scans show vulnerabilities at the moment they run, but networks change constantly. New devices connect, software updates install, and configurations change daily.
No Real-Time Protection: A scan might identify that your remote desktop protocol is exposed, but it won't stop an attacker from exploiting that weakness at 3 AM while you're sleeping.
False Security Confidence: Clean scan results create dangerous complacency. Business owners assume their systems are secure because their quarterly report looks good, while threats evolve and multiply between scans.
How Network Monitoring Stops Ransomware in Its Tracks
Network monitoring takes a fundamentally different approach: instead of looking for potential problems, it watches for actual threats.
When ransomware infects a Connecticut business, it follows predictable patterns:
- Initial compromise through email, web browsing, or remote access
- Lateral movement as malware spreads to other network devices
- Data encryption as files get systematically locked
- Command and control communication with attackers' servers
Network monitoring catches these attacks during steps 1 and 2: before your data gets encrypted.
A local Connecticut law firm invested in comprehensive network monitoring after hearing about industry ransomware attacks. Six months later, their system detected unusual file access patterns at 11 PM on a Friday. The monitoring system immediately isolated the affected workstation and alerted their IT team.
Investigation revealed that an employee's compromised credentials were being used to access client files remotely. Without network monitoring, this would have become a full-scale ransomware attack affecting hundreds of confidential legal documents.

The Numbers Don't Lie: Network Monitoring vs. Ransomware
Vulnerability Scanning Success Rate: 23% of businesses with regular vulnerability scans still experience successful ransomware attacks
Network Monitoring Success Rate: 89% of businesses with 24/7 network monitoring detect and stop ransomware before data encryption begins
Average Recovery Time:
- Vulnerability scanning only: 23 days to full operations
- Network monitoring: 4 hours to full operations
Average Total Cost:
- Vulnerability scanning only: $187,000 per incident
- Network monitoring: $12,000 per incident
The math is simple: network monitoring costs less and protects better.
The Smart Connecticut SMB Strategy
Here's the truth most cybersecurity vendors won't tell you: you need both vulnerability scanning and network monitoring, but if you can only afford one, choose monitoring.
Start with network monitoring because it provides immediate protection against active threats. Add quarterly vulnerability scanning once your monitoring system is established to identify and fix weaknesses proactively.
For Connecticut SMBs with limited budgets, prioritize:
- 24/7 network monitoring with automated threat response
- Employee security training focused on email and web threats
- Quarterly vulnerability scans to identify system weaknesses
- Incident response planning for when attacks succeed
The Bottom Line for Connecticut Business Owners
Ransomware attacks aren't slowing down: they're accelerating. Connecticut businesses can't afford to choose the wrong cybersecurity approach.
Vulnerability scanning tells you what might go wrong. Network monitoring stops things from going wrong.
Your business survives on uptime, not reports. When attackers target your company at 2 AM, you need systems that fight back automatically, not quarterly reports that sit in your email inbox.
The 300% increase in SMB ransomware isn't a distant threat: it's happening to Connecticut businesses right now. The question isn't whether you'll be targeted. It's whether you'll be protected when they come.
Choose the security strategy that works when you're not watching.
Ready to implement 24/7 network monitoring for your Connecticut business? FoxPowerIT provides network monitoring and vulnerability scanning services designed specifically for SMBs. Get your free security assessment today.
Is Your Microsoft 365 Migration Actually Making You LESS Secure? Here's What 73% of Connecticut SMBs Get Wrong

Your IT consultant just finished migrating your Connecticut business to Microsoft 365. Your team can access email anywhere. Files sync automatically. Collaboration is smoother than ever.
Three weeks later, you get a call from your biggest client: "Someone's been sending phishing emails from your company's email address. We're suspending our contract until you fix this security breach."
Welcome to the hidden danger of Microsoft 365 migrations gone wrong.
73% of Connecticut SMBs make their businesses less secure when they migrate to Microsoft 365: not because the platform is inherently risky, but because they misconfigure security settings during the transition. The same flexibility that makes M365 powerful also makes it dangerous in the wrong hands.
The Migration Security Paradox
Microsoft 365 can be more secure than on-premises email systems: or it can be a digital disaster waiting to happen. The difference comes down to configuration choices most business owners don't even know they're making.
Here's what happens in a typical Connecticut SMB migration:
Your IT provider moves your email, sets up file sharing, enables Teams collaboration, and declares the project complete. Everyone can work. Everything functions. The migration is "successful."
But behind the scenes, your security posture has quietly degraded:
- Multi-factor authentication remains disabled for "user convenience"
- Email forwarding rules allow automatic redirection to external addresses
- File sharing permissions default to "anyone with the link can edit"
- Admin accounts use the same passwords as before migration
Your systems work perfectly: for legitimate users and attackers alike.

The 7 Security Mistakes That Doom M365 Migrations
Mistake #1: Skipping Multi-Factor Authentication (MFA)
63% of successful email breaches target M365 accounts without MFA enabled. Yet most Connecticut businesses disable MFA because "it's inconvenient for users."
MFA prevents 99.9% of automated attacks even when passwords are compromised. Skipping it is like installing a state-of-the-art security system and leaving your front door unlocked.
Mistake #2: Using Default Sharing Settings
M365's default file sharing settings prioritize ease of use over security. Files shared via email links often remain accessible indefinitely to anyone who clicks them: including former employees, competitors, or attackers who intercept communications.
Mistake #3: Ignoring Email Security Policies
Standard M365 email security blocks obvious spam but allows sophisticated phishing attempts through. Advanced Threat Protection and Safe Attachments features remain disabled in 78% of SMB deployments because they're "add-on costs."
Mistake #4: No Admin Account Monitoring
M365 admin accounts have unlimited access to your organization's data, settings, and users. Most businesses don't monitor admin account activity, so compromised administrative credentials can operate undetected for months.
Mistake #5: Weak Password Policies
M365 allows password policies as weak as 8-character passwords with no complexity requirements. Many migrations keep existing weak password standards instead of implementing stronger authentication requirements.
Mistake #6: Unmanaged Device Access
M365 works on any device with an internet connection: including personal smartphones, tablets, and home computers. Without device management policies, company data flows to uncontrolled devices outside your security perimeter.
Mistake #7: No Security Monitoring
M365 generates detailed security logs showing login attempts, file access, permission changes, and suspicious activities. But 84% of Connecticut SMBs never configure monitoring alerts or review security reports.

The Secure M365 Migration Checklist
Phase 1: Pre-Migration Security Planning
- Document current security policies and requirements
- Plan MFA rollout strategy for all users
- Define file sharing and collaboration policies
- Establish admin account management procedures
Phase 2: Secure Migration Configuration
- Enable MFA for all accounts before migration completion
- Configure Advanced Threat Protection for email security
- Set restrictive default sharing permissions for files
- Implement conditional access policies for device management
Phase 3: Post-Migration Security Hardening
- Review and adjust all default security settings
- Configure security monitoring and alerting
- Establish regular security auditing procedures
- Train users on new security features and policies
Phase 4: Ongoing Security Management
- Monthly security posture reviews
- Quarterly access permission audits
- Annual security policy updates
- Continuous user security training
The Hidden Cost of Insecure M365
A poorly secured M365 deployment doesn't just risk data breaches: it creates ongoing business vulnerabilities that compound over time.
Email Compromise: Attackers use compromised M365 accounts to send convincing phishing emails to customers, vendors, and employees. Victims trust emails from your domain, making attacks more successful.
Data Exposure: Overshared files in SharePoint and OneDrive can be accessed by unauthorized users indefinitely. Sensitive business information, customer data, and financial records become accessible to anyone with shared links.
Compliance Violations: Industries with regulatory requirements (healthcare, finance, legal) face severe penalties when M365 misconfigurations expose protected data.
Productivity Disruption: Security incidents force business interruptions while IT teams investigate breaches, reset compromised accounts, and restore damaged systems.
The Right Way to Migrate to M365
Successful M365 migrations prioritize security from day one, not as an afterthought.
Week 1: Plan security requirements and policies
Week 2: Configure secure baseline settings
Week 3: Migrate data with security controls enabled
Week 4: Test security features and train users
Week 5: Implement monitoring and ongoing management
The businesses that invest extra time in secure configuration save money, reputation, and customer trust long-term.
The Bottom Line for Connecticut SMBs
Microsoft 365 can transform your business productivity: or transform your business into an easy target for cybercriminals.
The difference is in the details. Default settings prioritize convenience over security. Proper configuration requires deliberate choices that protect your business without hampering productivity.
Your migration isn't complete until your security is configured correctly. A working M365 system isn't the same as a secure M365 system.
73% of Connecticut businesses get this wrong during migration. Don't be part of that statistic.
The stakes are too high, and the fixes are too straightforward to accept unnecessary risk.
Planning a Microsoft 365 migration? FoxPowerIT specializes in secure M365 deployments for Connecticut SMBs. Our security management services ensure your migration enhances both productivity and protection. Contact us for your secure migration consultation.
Defense in Depth Cybersecurity Explained in Under 3 Minutes: The Connecticut SMB Owner's Guide to Stopping AI-Driven Attacks

Your business has a firewall, antivirus software, and employee training. You feel protected. Then you get the call: "We've been breached. Customer data is compromised. Our systems are down."
How did attackers get through three layers of security?
Simple: they didn't break through your defenses: they walked around them.
AI-driven cyberattacks are rewriting the rules of business security. Attackers now use machine learning to find weaknesses faster than humans can patch them, create personalized phishing emails that fool trained employees, and develop malware that evolves faster than traditional detection systems.
Connecticut SMBs face a choice: adapt your security strategy or become another statistic in the 67% of small businesses that experience successful cyberattacks within the next year.
Why Single-Point Security Fails Against AI
Traditional cybersecurity works like a castle wall: strong, impressive, and completely useless once attackers find a way over, under, or around it.
Most Connecticut businesses protect themselves with:
- Perimeter security (firewalls and intrusion detection)
- Endpoint protection (antivirus and anti-malware)
- User training (phishing awareness and password policies)
Each layer works well against traditional attacks. But AI-powered attacks don't follow traditional patterns.
AI can:
- Analyze your network to find the weakest entry point
- Craft personalized attacks using data from social media and data breaches
- Adapt in real-time when one attack method fails
- Move laterally through networks faster than human defenders can respond
When your security depends on any single point of failure, AI will find and exploit it.
Defense in Depth: The 3-Minute Explanation
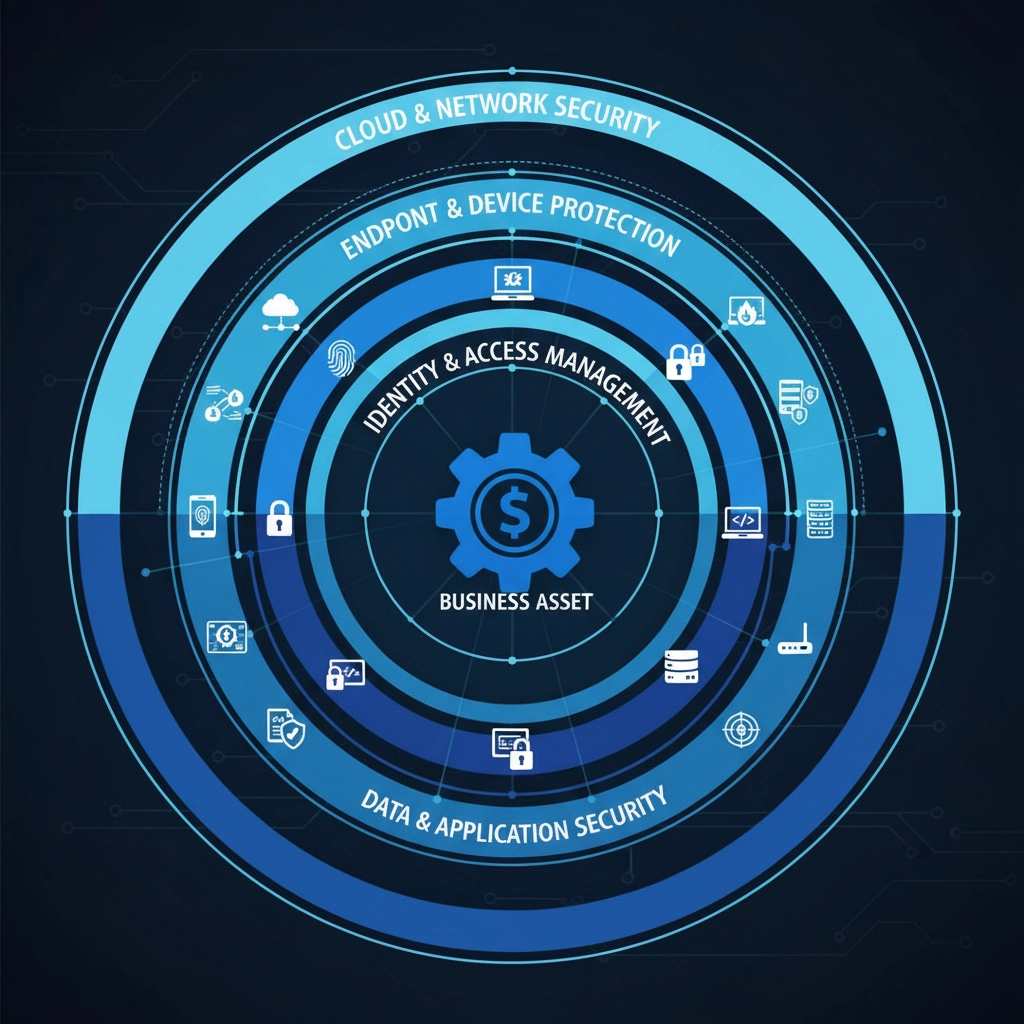
Defense in Depth isn't about building stronger walls: it's about building multiple independent barriers that work together.
Think of it like protecting your home:
- Perimeter: Locked fence and security cameras
- Access: Deadbolt locks and alarm system
- Interior: Motion sensors and safe for valuables
- Response: Direct connection to security company
If an intruder defeats the fence, they still face locks. If they bypass the locks, alarms activate. If they disable alarms, motion sensors trigger. Each failure activates the next layer of protection.
Cybersecurity works the same way, but with digital barriers:
Layer 1: Network Perimeter
- Firewalls block unauthorized network access
- Intrusion detection systems monitor traffic patterns
- VPN access controls who can connect remotely
Layer 2: Device Security
- Endpoint detection and response on all computers
- Mobile device management for smartphones and tablets
- Regular security updates and patch management
Layer 3: Access Controls
- Multi-factor authentication for all accounts
- Role-based permissions limiting data access
- Privileged account monitoring for admin users
Layer 4: Data Protection
- Encryption for sensitive information at rest and in transit
- Data loss prevention to stop unauthorized sharing
- Regular backups with tested recovery procedures
Layer 5: Human Defenses
- Security awareness training updated for AI threats
- Incident response procedures for quick attack containment
- Regular security assessments to identify new vulnerabilities
How Defense in Depth Stops AI-Driven Attacks
Scenario: AI-powered phishing targets your accounting manager with a personalized email appearing to come from your CEO, requesting urgent wire transfer authorization.
Single-layer defense: Employee training might catch obvious phishing, but AI-crafted emails are increasingly sophisticated. If training fails, the attack succeeds.
Defense in Depth response:
- Layer 1: Email security filters flag suspicious sender patterns
- Layer 2: Multi-factor authentication prevents account access even if credentials are stolen
- Layer 3: Financial controls require dual approval for wire transfers
- Layer 4: Network monitoring detects unusual access patterns
- Layer 5: Incident response team investigates and contains potential threats
The attack must defeat five independent security layers to succeed. Even if three layers fail, two remaining barriers prevent disaster.

The Connecticut SMB Defense in Depth Strategy
Most Connecticut businesses think Defense in Depth requires massive IT budgets and dedicated security teams. Not true.
Phase 1: Essential Foundation (Month 1)
- Implement multi-factor authentication company-wide
- Deploy unified endpoint protection on all devices
- Establish automated backup and recovery procedures
- Create basic incident response communication plan
Phase 2: Enhanced Protection (Months 2-3)
- Add email security with advanced threat detection
- Configure network monitoring for unusual activity patterns
- Implement role-based access controls for sensitive data
- Develop employee security training program
Phase 3: Advanced Defense (Months 4-6)
- Deploy data loss prevention for confidential information
- Add privileged account monitoring for admin access
- Establish security assessment and vulnerability management
- Create comprehensive incident response and recovery procedures
The AI Advantage Works Both Ways
Here's the opportunity most businesses miss: AI doesn't just help attackers: it can supercharge your defenses too.
AI-powered security tools can:
- Detect unusual patterns faster than human analysts
- Respond to threats automatically at machine speed
- Learn from attack attempts to strengthen future defenses
- Predict vulnerabilities before attackers exploit them
The businesses that combine Defense in Depth strategy with AI-enhanced security tools will have decisive advantages over both traditional attackers and AI-powered threats.
Your 3-Minute Action Plan
Defense in Depth isn't a destination: it's a continuous improvement process that adapts as threats evolve.
This Week: Audit your current security layers. Where do you have single points of failure?
This Month: Implement the essential foundation layer that's missing from your current setup.
This Quarter: Build your comprehensive Defense in Depth strategy with professional guidance.
Connecticut businesses that wait for perfect security solutions will be compromised while they're waiting. The ones that start building layered defenses today will be protected while their competitors recover from attacks.
AI-driven threats are here now. Your layered defense should be too.
Ready to build your Defense in Depth cybersecurity strategy? FoxPowerIT provides comprehensive security management and infrastructure management services designed specifically for Connecticut SMBs. Schedule your security assessment today.

